make reviews clear again
47
SUMMARY.md
@ -164,29 +164,30 @@ GitHub 地址:https://github.com/firmianay/CTF-All-In-One
|
|||||||
* Malware
|
* Malware
|
||||||
* 7.2.x
|
* 7.2.x
|
||||||
* [八、学术篇](doc/8_academic.md)
|
* [八、学术篇](doc/8_academic.md)
|
||||||
* Return-Oriented Programming
|
* [8.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)](doc/8.1_ret2libc_without_func_calls.md)
|
||||||
* [8.1.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)](doc/8.1.1_return-into-libc_without_function_calls.md)
|
* [8.2 Return-Oriented Programming without Returns](doc/8.2_rop_without_returns.md)
|
||||||
* [8.1.2 Return-Oriented Programming without Returns](doc/8.1.2_rop_without_returns.md)
|
* [8.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms](doc/8.3_rop_rootkits.md)
|
||||||
* [8.1.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms](doc/8.1.3_return-oriented_rootkits.md)
|
* [8.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks](doc/8.4_ropdefender.md)
|
||||||
* [8.1.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks](doc/8.1.4_ropdefender.md)
|
* [8.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks](doc/8.5_dop.md)
|
||||||
* [8.1.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks](doc/8.1.5_data-oriented_programming.md)
|
* [8.6 Hacking Blind](doc/8.6_brop.md)
|
||||||
* [8.1.6 Hacking Blind](doc/8.1.6_hacking_blind.md)
|
* [8.7 What Cannot Be Read, Cannot Be Leveraged? Revisiting Assumptions of JIT-ROP Defenses](doc/8.7_jit-rop_defenses.md)
|
||||||
* Symbolic Execution
|
* [8.8 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)](doc/8.8_dynamic_taint_analysis.md)
|
||||||
* [8.2.1 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)](doc/8.2.1_dynamic_taint_analysis.md)
|
* [8.9 Symbolic Execution for Software Testing: Three Decades Later](doc/8.9_symbolic_execution.md)
|
||||||
* [8.2.2 Symbolic Execution for Software Testing: Three Decades Later](doc/8.2.2_symbolic_execution_for_software_testing.md)
|
* [8.10 AEG: Automatic Exploit Generation](doc/8.10_aeg.md)
|
||||||
* [8.2.3 AEG: Automatic Exploit Generation](doc/8.2.3_automatic_exploit_generation.md)
|
* [8.11 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software](doc/8.11_aslp.md)
|
||||||
* Address Space Layout Randomization
|
* [8.12 ASLR on the Line: Practical Cache Attacks on the MMU](doc/8.12_aslr_on_the_line.md)
|
||||||
* [8.3.1 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software](doc/8.3.1_aslp.md)
|
* [8.13 New Frontiers of Reverse Engineering](doc/8.13_reverse_engineering.md)
|
||||||
* Code Obfuscation
|
* [8.14 Who Allocated My Memory? Detecting Custom Memory Allocators in C Binaries](doc/8.14_detecting_memory_allocators.md)
|
||||||
* Reverse Engineering
|
* [8.15 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning](doc/8.15_emulator_vs_real_phone.md)
|
||||||
* [8.3 New Frontiers of Reverse Engineering](doc/8.3_new_frontiers_of_reverse_engineering.md)
|
* [8.16 DynaLog: An automated dynamic analysis framework for characterizing Android applications](doc/8.16_dynalog.md)
|
||||||
* Android Security
|
* [8.17 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls](doc/8.17_actual_used_permissions.md)
|
||||||
* [8.4 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning](doc/8.4_emulator_vs_real_phone.md)
|
* [8.18 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models](doc/8.18_malware_markov_chains.md)
|
||||||
* [8.5 DynaLog: An automated dynamic analysis framework for characterizing Android applications](doc/8.5_dynalog_an_automated_dynamic_analysis_framework.md)
|
* [8.19 DroidNative: Semantic-Based Detection of Android Native Code Malware](doc/8.19_droidnative.md)
|
||||||
* [8.6 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls](doc/8.6_malware_detection_based_on_actual_used_permissions.md)
|
* [8.20 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware](doc/8.20_droidanalytics.md)
|
||||||
* [8.7 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models](doc/8.7_detecting_malware_by_building_markov_chains.md)
|
* [8.21 Micro-Virtualization Memory Tracing to Detect and Prevent Spraying Attacks](doc/8.21_tracing_to_detect_spraying.md)
|
||||||
* [8.8 DroidNative: Semantic-Based Detection of Android Native Code Malware](doc/8.8_droidnative_semantic-based_detection_of_android_native_code_malware.md)
|
* [8.22 Practical Memory Checking With Dr. Memory](doc/8.22_memory_checking.md)
|
||||||
* [8.9 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware](doc/8.9_droidanalytics_signature_based_analytic_system.md)
|
* [8.23 Evaluating the Effectiveness of Current Anti-ROP Defenses](doc/8.23_current_anti-rop.md)
|
||||||
|
* [8.24 How to Make ASLR Win the Clone Wars: Runtime Re-Randomization](doc/8.24_runtime_re-randomization.md)
|
||||||
* [九、附录](doc/9_appendix.md)
|
* [九、附录](doc/9_appendix.md)
|
||||||
* [9.1 更多 Linux 工具](doc/9.1_Linuxtools.md)
|
* [9.1 更多 Linux 工具](doc/9.1_Linuxtools.md)
|
||||||
* [9.2 更多 Windows 工具](doc/9.2_wintools.md)
|
* [9.2 更多 Windows 工具](doc/9.2_wintools.md)
|
||||||
|
|||||||
@ -17,6 +17,18 @@ $ make && sudo make install
|
|||||||
|
|
||||||
|
|
||||||
## 常用选项
|
## 常用选项
|
||||||
|
使用 `gcc -v` 可以查看默认开启的选项:
|
||||||
|
```
|
||||||
|
$ gcc -v
|
||||||
|
Using built-in specs.
|
||||||
|
COLLECT_GCC=gcc
|
||||||
|
COLLECT_LTO_WRAPPER=/usr/lib/gcc/x86_64-linux-gnu/5/lto-wrapper
|
||||||
|
Target: x86_64-linux-gnu
|
||||||
|
Configured with: ../src/configure -v --with-pkgversion='Ubuntu 5.4.0-6ubuntu1~16.04.9' --with-bugurl=file:///usr/share/doc/gcc-5/README.Bugs --enable-languages=c,ada,c++,java,go,d,fortran,objc,obj-c++ --prefix=/usr --program-suffix=-5 --enable-shared --enable-linker-build-id --libexecdir=/usr/lib --without-included-gettext --enable-threads=posix --libdir=/usr/lib --enable-nls --with-sysroot=/ --enable-clocale=gnu --enable-libstdcxx-debug --enable-libstdcxx-time=yes --with-default-libstdcxx-abi=new --enable-gnu-unique-object --disable-vtable-verify --enable-libmpx --enable-plugin --with-system-zlib --disable-browser-plugin --enable-java-awt=gtk --enable-gtk-cairo --with-java-home=/usr/lib/jvm/java-1.5.0-gcj-5-amd64/jre --enable-java-home --with-jvm-root-dir=/usr/lib/jvm/java-1.5.0-gcj-5-amd64 --with-jvm-jar-dir=/usr/lib/jvm-exports/java-1.5.0-gcj-5-amd64 --with-arch-directory=amd64 --with-ecj-jar=/usr/share/java/eclipse-ecj.jar --enable-objc-gc --enable-multiarch --disable-werror --with-arch-32=i686 --with-abi=m64 --with-multilib-list=m32,m64,mx32 --enable-multilib --with-tune=generic --enable-checking=release --build=x86_64-linux-gnu --host=x86_64-linux-gnu --target=x86_64-linux-gnu
|
||||||
|
Thread model: posix
|
||||||
|
gcc version 5.4.0 20160609 (Ubuntu 5.4.0-6ubuntu1~16.04.9)
|
||||||
|
```
|
||||||
|
|
||||||
#### 控制标准版本的编译选项
|
#### 控制标准版本的编译选项
|
||||||
- `-ansi`:告诉编译器遵守 C 语言的 ISO C90 标准。
|
- `-ansi`:告诉编译器遵守 C 语言的 ISO C90 标准。
|
||||||
- `-std=`:通过使用一个参数来设置需要的标准。
|
- `-std=`:通过使用一个参数来设置需要的标准。
|
||||||
|
|||||||
@ -19,9 +19,349 @@ $ strings libc-2.19.so | grep "GNU C"
|
|||||||
GNU C Library (Debian GLIBC 2.19-18+deb8u6) stable release version 2.19, by Roland McGrath et al.
|
GNU C Library (Debian GLIBC 2.19-18+deb8u6) stable release version 2.19, by Roland McGrath et al.
|
||||||
Compiled by GNU CC version 4.8.4.
|
Compiled by GNU CC version 4.8.4.
|
||||||
```
|
```
|
||||||
|
32 位程序,开启了 canary 和 NX。
|
||||||
|
|
||||||
|
在 Ubuntu-14.04 上玩一下,添加 user 和显示 user:
|
||||||
|
```
|
||||||
|
$ ./babyfengshui
|
||||||
|
0: Add a user
|
||||||
|
1: Delete a user
|
||||||
|
2: Display a user
|
||||||
|
3: Update a user description
|
||||||
|
4: Exit
|
||||||
|
Action: 0
|
||||||
|
size of description: 10 # description 最大长度(desc_size)
|
||||||
|
name: AAAA
|
||||||
|
text length: 5 # description 实际长度(text_size)
|
||||||
|
text: aaaa
|
||||||
|
0: Add a user
|
||||||
|
1: Delete a user
|
||||||
|
2: Display a user
|
||||||
|
3: Update a user description
|
||||||
|
4: Exit
|
||||||
|
Action: 2
|
||||||
|
index: 0
|
||||||
|
name: AAAA
|
||||||
|
description: aaaa
|
||||||
|
```
|
||||||
|
对于 description 的调整只能在最大长度的范围内,否则程序退出:
|
||||||
|
```
|
||||||
|
0: Add a user
|
||||||
|
1: Delete a user
|
||||||
|
2: Display a user
|
||||||
|
3: Update a user description
|
||||||
|
4: Exit
|
||||||
|
Action: 3
|
||||||
|
index: 0
|
||||||
|
text length: 20
|
||||||
|
my l33t defenses cannot be fooled, cya!
|
||||||
|
```
|
||||||
|
|
||||||
|
|
||||||
## 题目解析
|
## 题目解析
|
||||||
|
#### Add a user
|
||||||
|
```
|
||||||
|
[0x080485c0]> pdf @ sub.malloc_816
|
||||||
|
/ (fcn) sub.malloc_816 239
|
||||||
|
| sub.malloc_816 (int arg_8h);
|
||||||
|
| ; var int local_1ch @ ebp-0x1c
|
||||||
|
| ; var int local_14h @ ebp-0x14
|
||||||
|
| ; var int local_10h @ ebp-0x10
|
||||||
|
| ; var int local_ch @ ebp-0xc
|
||||||
|
| ; arg int arg_8h @ ebp+0x8
|
||||||
|
| ; CALL XREF from 0x08048b21 (main)
|
||||||
|
| 0x08048816 push ebp
|
||||||
|
| 0x08048817 mov ebp, esp
|
||||||
|
| 0x08048819 sub esp, 0x28 ; '('
|
||||||
|
| 0x0804881c mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8
|
||||||
|
| 0x0804881f mov dword [local_1ch], eax ; 将参数 desc_size 放到 [local_1ch]
|
||||||
|
| 0x08048822 mov eax, dword gs:[0x14] ; [0x14:4]=-1 ; 20
|
||||||
|
| 0x08048828 mov dword [local_ch], eax
|
||||||
|
| 0x0804882b xor eax, eax
|
||||||
|
| 0x0804882d sub esp, 0xc
|
||||||
|
| 0x08048830 push dword [local_1ch]
|
||||||
|
| 0x08048833 call sym.imp.malloc ; [local_14h] = malloc(desc_size) 为 description 分配空间
|
||||||
|
| 0x08048838 add esp, 0x10
|
||||||
|
| 0x0804883b mov dword [local_14h], eax
|
||||||
|
| 0x0804883e sub esp, 4
|
||||||
|
| 0x08048841 push dword [local_1ch]
|
||||||
|
| 0x08048844 push 0
|
||||||
|
| 0x08048846 push dword [local_14h]
|
||||||
|
| 0x08048849 call sym.imp.memset ; memset([local_14h], 0, desc_size) 初始化
|
||||||
|
| 0x0804884e add esp, 0x10
|
||||||
|
| 0x08048851 sub esp, 0xc
|
||||||
|
| 0x08048854 push 0x80 ; 128
|
||||||
|
| 0x08048859 call sym.imp.malloc ; [local_10h] = malloc(0x80) 为 user struct 分配空间
|
||||||
|
| 0x0804885e add esp, 0x10
|
||||||
|
| 0x08048861 mov dword [local_10h], eax
|
||||||
|
| 0x08048864 sub esp, 4
|
||||||
|
| 0x08048867 push 0x80 ; 128
|
||||||
|
| 0x0804886c push 0
|
||||||
|
| 0x0804886e push dword [local_10h]
|
||||||
|
| 0x08048871 call sym.imp.memset ; memset([local_10h], 0, 0x80) 初始化
|
||||||
|
| 0x08048876 add esp, 0x10
|
||||||
|
| 0x08048879 mov eax, dword [local_10h]
|
||||||
|
| 0x0804887c mov edx, dword [local_14h]
|
||||||
|
| 0x0804887f mov dword [eax], edx ; user->desc = desc ; desc = [local_14h]
|
||||||
|
| 0x08048881 movzx eax, byte [0x804b069] ; [0x804b069:1]=0 ; 取出序号 i
|
||||||
|
| 0x08048888 movzx eax, al
|
||||||
|
| 0x0804888b mov edx, dword [local_10h]
|
||||||
|
| 0x0804888e mov dword [eax*4 + 0x804b080], edx ; store[i] = user 将 user 放到数组里
|
||||||
|
| 0x08048895 sub esp, 0xc
|
||||||
|
| 0x08048898 push str.name: ; 0x8048cf3 ; "name: "
|
||||||
|
| 0x0804889d call sym.imp.printf ; int printf(const char *format)
|
||||||
|
| 0x080488a2 add esp, 0x10
|
||||||
|
| 0x080488a5 movzx eax, byte [0x804b069] ; [0x804b069:1]=0
|
||||||
|
| 0x080488ac movzx eax, al
|
||||||
|
| 0x080488af mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| 0x080488b6 add eax, 4 ; 取出 store[i]->name
|
||||||
|
| 0x080488b9 sub esp, 8
|
||||||
|
| 0x080488bc push 0x7c ; '|' ; 124
|
||||||
|
| 0x080488be push eax
|
||||||
|
| 0x080488bf call sub.fgets_6bb ; 读入 0x7c 个字符到 store[i]->name,将末尾的 '\n' 换成 '\x00'
|
||||||
|
| 0x080488c4 add esp, 0x10
|
||||||
|
| 0x080488c7 movzx eax, byte [0x804b069] ; [0x804b069:1]=0
|
||||||
|
| 0x080488ce add eax, 1 ; 序号 i = i + 1
|
||||||
|
| 0x080488d1 mov byte [0x804b069], al ; [0x804b069:1]=0 ; 写回去
|
||||||
|
| 0x080488d6 movzx eax, byte [0x804b069] ; [0x804b069:1]=0 ; 取出 i
|
||||||
|
| 0x080488dd sub eax, 1 ; i = i - 1
|
||||||
|
| 0x080488e0 movzx eax, al
|
||||||
|
| 0x080488e3 sub esp, 0xc
|
||||||
|
| 0x080488e6 push eax
|
||||||
|
| 0x080488e7 call sub.text_length:_724 ; 调用更新 description 的函数,参数为 i
|
||||||
|
| 0x080488ec add esp, 0x10
|
||||||
|
| 0x080488ef mov eax, dword [local_10h]
|
||||||
|
| 0x080488f2 mov ecx, dword [local_ch]
|
||||||
|
| 0x080488f5 xor ecx, dword gs:[0x14]
|
||||||
|
| ,=< 0x080488fc je 0x8048903
|
||||||
|
| | 0x080488fe call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)
|
||||||
|
| | ; JMP XREF from 0x080488fc (sub.malloc_816)
|
||||||
|
| `-> 0x08048903 leave
|
||||||
|
\ 0x08048904 ret
|
||||||
|
```
|
||||||
|
函数首先分配一个 description 的最大空间,然后分配 user 结构体空间,并将 user 放到 store 数组中,最后调用更新 description 的函数。
|
||||||
|
|
||||||
|
user 结构体和 store 数组如下:
|
||||||
|
```c
|
||||||
|
struct user {
|
||||||
|
char *desc;
|
||||||
|
char name[0x7c];
|
||||||
|
} user;
|
||||||
|
|
||||||
|
struct user *store[50];
|
||||||
|
```
|
||||||
|
store 放在 `0x804b080`,当前 user 个数 user_num 放在 `0x804b069`。
|
||||||
|
|
||||||
|
#### Delete a user
|
||||||
|
```
|
||||||
|
[0x080485c0]> pdf @ sub.free_905
|
||||||
|
/ (fcn) sub.free_905 138
|
||||||
|
| sub.free_905 (int arg_8h);
|
||||||
|
| ; var int local_1ch @ ebp-0x1c
|
||||||
|
| ; var int local_ch @ ebp-0xc
|
||||||
|
| ; arg int arg_8h @ ebp+0x8
|
||||||
|
| ; CALL XREF from 0x08048b5f (main)
|
||||||
|
| 0x08048905 push ebp
|
||||||
|
| 0x08048906 mov ebp, esp
|
||||||
|
| 0x08048908 sub esp, 0x28 ; '('
|
||||||
|
| 0x0804890b mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8
|
||||||
|
| 0x0804890e mov byte [local_1ch], al ; 将参数 i 放到 [local_1ch]
|
||||||
|
| 0x08048911 mov eax, dword gs:[0x14] ; [0x14:4]=-1 ; 20
|
||||||
|
| 0x08048917 mov dword [local_ch], eax
|
||||||
|
| 0x0804891a xor eax, eax
|
||||||
|
| 0x0804891c movzx eax, byte [0x804b069] ; [0x804b069:1]=0 ; 取出 user_num
|
||||||
|
| 0x08048923 cmp byte [local_1ch], al ; [0x2:1]=255 ; 2 ; 比较
|
||||||
|
| ,=< 0x08048926 jae 0x8048978 ; i 大于等于 user_num 时函数返回
|
||||||
|
| | 0x08048928 movzx eax, byte [local_1ch]
|
||||||
|
| | 0x0804892c mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| | 0x08048933 test eax, eax ; store[i] 为 0 是函数返回
|
||||||
|
| ,==< 0x08048935 je 0x804897b
|
||||||
|
| || 0x08048937 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x0804893b mov eax, dword [eax*4 + 0x804b080] ; [0x804b080:4]=0
|
||||||
|
| || 0x08048942 mov eax, dword [eax] ; 取出 store[i]->desc
|
||||||
|
| || 0x08048944 sub esp, 0xc
|
||||||
|
| || 0x08048947 push eax
|
||||||
|
| || 0x08048948 call sym.imp.free ; free(store[i]->desc) 释放 description
|
||||||
|
| || 0x0804894d add esp, 0x10
|
||||||
|
| || 0x08048950 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x08048954 mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| || 0x0804895b sub esp, 0xc
|
||||||
|
| || 0x0804895e push eax
|
||||||
|
| || 0x0804895f call sym.imp.free ; free(store[i]) 释放 user
|
||||||
|
| || 0x08048964 add esp, 0x10
|
||||||
|
| || 0x08048967 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x0804896b mov dword [eax*4 + 0x804b080], 0 ; 将 store[i] 置为 0
|
||||||
|
| ,===< 0x08048976 jmp 0x804897c
|
||||||
|
| ||| ; JMP XREF from 0x08048926 (sub.free_905)
|
||||||
|
| ||`-> 0x08048978 nop
|
||||||
|
| ||,=< 0x08048979 jmp 0x804897c
|
||||||
|
| ||| ; JMP XREF from 0x08048935 (sub.free_905)
|
||||||
|
| |`--> 0x0804897b nop
|
||||||
|
| | | ; JMP XREF from 0x08048979 (sub.free_905)
|
||||||
|
| | | ; JMP XREF from 0x08048976 (sub.free_905)
|
||||||
|
| `-`-> 0x0804897c mov eax, dword [local_ch]
|
||||||
|
| 0x0804897f xor eax, dword gs:[0x14]
|
||||||
|
| ,=< 0x08048986 je 0x804898d
|
||||||
|
| | 0x08048988 call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)
|
||||||
|
| | ; JMP XREF from 0x08048986 (sub.free_905)
|
||||||
|
| `-> 0x0804898d leave
|
||||||
|
\ 0x0804898e ret
|
||||||
|
```
|
||||||
|
删除的过程将 description 和 user 依次释放,并将 store[i] 置为 0。
|
||||||
|
|
||||||
|
但是 user->desc 没有被置为 0,user_num 也没有减 1,似乎可能导致 UAF,但不知道怎么用。
|
||||||
|
|
||||||
|
#### Display a user
|
||||||
|
```
|
||||||
|
[0x080485c0]> pdf @ sub.name:__s_98f
|
||||||
|
/ (fcn) sub.name:__s_98f 136
|
||||||
|
| sub.name:__s_98f (int arg_8h);
|
||||||
|
| ; var int local_1ch @ ebp-0x1c
|
||||||
|
| ; var int local_ch @ ebp-0xc
|
||||||
|
| ; arg int arg_8h @ ebp+0x8
|
||||||
|
| ; CALL XREF from 0x08048b9d (main)
|
||||||
|
| 0x0804898f push ebp
|
||||||
|
| 0x08048990 mov ebp, esp
|
||||||
|
| 0x08048992 sub esp, 0x28 ; '('
|
||||||
|
| 0x08048995 mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8
|
||||||
|
| 0x08048998 mov byte [local_1ch], al ; 将参数 i 放到 [local_1ch]
|
||||||
|
| 0x0804899b mov eax, dword gs:[0x14] ; [0x14:4]=-1 ; 20
|
||||||
|
| 0x080489a1 mov dword [local_ch], eax
|
||||||
|
| 0x080489a4 xor eax, eax
|
||||||
|
| 0x080489a6 movzx eax, byte [0x804b069] ; [0x804b069:1]=0 ; 取出 user_num
|
||||||
|
| 0x080489ad cmp byte [local_1ch], al ; [0x2:1]=255 ; 2 ; 比较
|
||||||
|
| ,=< 0x080489b0 jae 0x8048a00 ; i 大于等于 user_num 时函数返回
|
||||||
|
| | 0x080489b2 movzx eax, byte [local_1ch]
|
||||||
|
| | 0x080489b6 mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| | 0x080489bd test eax, eax
|
||||||
|
| ,==< 0x080489bf je 0x8048a03 ; store[i] 为 0 时函数返回
|
||||||
|
| || 0x080489c1 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x080489c5 mov eax, dword [eax*4 + 0x804b080] ; [0x804b080:4]=0
|
||||||
|
| || 0x080489cc add eax, 4 ; 取出 store[i]->name
|
||||||
|
| || 0x080489cf sub esp, 8
|
||||||
|
| || 0x080489d2 push eax
|
||||||
|
| || 0x080489d3 push str.name:__s ; 0x8048cfa ; "name: %s\n"
|
||||||
|
| || 0x080489d8 call sym.imp.printf ; 打印 store[i]->name
|
||||||
|
| || 0x080489dd add esp, 0x10
|
||||||
|
| || 0x080489e0 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x080489e4 mov eax, dword [eax*4 + 0x804b080] ; [0x804b080:4]=0
|
||||||
|
| || 0x080489eb mov eax, dword [eax] ; 取出 store[i]->desc
|
||||||
|
| || 0x080489ed sub esp, 8
|
||||||
|
| || 0x080489f0 push eax
|
||||||
|
| || 0x080489f1 push str.description:__s ; 0x8048d04 ; "description: %s\n"
|
||||||
|
| || 0x080489f6 call sym.imp.printf ; 打印 store[i]->desc
|
||||||
|
| || 0x080489fb add esp, 0x10
|
||||||
|
| ,===< 0x080489fe jmp 0x8048a04
|
||||||
|
| ||| ; JMP XREF from 0x080489b0 (sub.name:__s_98f)
|
||||||
|
| ||`-> 0x08048a00 nop
|
||||||
|
| ||,=< 0x08048a01 jmp 0x8048a04
|
||||||
|
| ||| ; JMP XREF from 0x080489bf (sub.name:__s_98f)
|
||||||
|
| |`--> 0x08048a03 nop
|
||||||
|
| | | ; JMP XREF from 0x08048a01 (sub.name:__s_98f)
|
||||||
|
| | | ; JMP XREF from 0x080489fe (sub.name:__s_98f)
|
||||||
|
| `-`-> 0x08048a04 mov eax, dword [local_ch]
|
||||||
|
| 0x08048a07 xor eax, dword gs:[0x14]
|
||||||
|
| ,=< 0x08048a0e je 0x8048a15
|
||||||
|
| | 0x08048a10 call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)
|
||||||
|
| | ; JMP XREF from 0x08048a0e (sub.name:__s_98f)
|
||||||
|
| `-> 0x08048a15 leave
|
||||||
|
\ 0x08048a16 ret
|
||||||
|
```
|
||||||
|
函数首先判断 store[i] 是否存在,如果是,就打印出 name 和 description。
|
||||||
|
|
||||||
|
#### Update a user description
|
||||||
|
```
|
||||||
|
[0x080485c0]> pdf @ sub.text_length:_724
|
||||||
|
/ (fcn) sub.text_length:_724 242
|
||||||
|
| sub.text_length:_724 (int arg_8h);
|
||||||
|
| ; var int local_1ch @ ebp-0x1c
|
||||||
|
| ; var int local_11h @ ebp-0x11
|
||||||
|
| ; var int local_10h @ ebp-0x10
|
||||||
|
| ; var int local_ch @ ebp-0xc
|
||||||
|
| ; arg int arg_8h @ ebp+0x8
|
||||||
|
| ; CALL XREF from 0x08048bdb (main)
|
||||||
|
| ; CALL XREF from 0x080488e7 (sub.malloc_816)
|
||||||
|
| 0x08048724 push ebp
|
||||||
|
| 0x08048725 mov ebp, esp
|
||||||
|
| 0x08048727 sub esp, 0x28 ; '('
|
||||||
|
| 0x0804872a mov eax, dword [arg_8h] ; [0x8:4]=-1 ; 8
|
||||||
|
| 0x0804872d mov byte [local_1ch], al ; 将参数 i 放到 [local_1ch]
|
||||||
|
| 0x08048730 mov eax, dword gs:[0x14] ; [0x14:4]=-1 ; 20
|
||||||
|
| 0x08048736 mov dword [local_ch], eax
|
||||||
|
| 0x08048739 xor eax, eax
|
||||||
|
| 0x0804873b movzx eax, byte [0x804b069] ; [0x804b069:1]=0 ; 取出 user_num
|
||||||
|
| 0x08048742 cmp byte [local_1ch], al ; [0x2:1]=255 ; 2 ; 比较
|
||||||
|
| ,=< 0x08048745 jae 0x80487ff ; i 大于等于 user_num 时函数返回
|
||||||
|
| | 0x0804874b movzx eax, byte [local_1ch]
|
||||||
|
| | 0x0804874f mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| | 0x08048756 test eax, eax
|
||||||
|
| ,==< 0x08048758 je 0x8048802 ; store[i] 为 0 时函数返回
|
||||||
|
| || 0x0804875e mov dword [local_10h], 0 ; text_size 放到 [local_10h]
|
||||||
|
| || 0x08048765 sub esp, 0xc
|
||||||
|
| || 0x08048768 push str.text_length: ; 0x8048cb0 ; "text length: "
|
||||||
|
| || 0x0804876d call sym.imp.printf ; int printf(const char *format)
|
||||||
|
| || 0x08048772 add esp, 0x10
|
||||||
|
| || 0x08048775 sub esp, 4
|
||||||
|
| || 0x08048778 lea eax, [local_11h]
|
||||||
|
| || 0x0804877b push eax
|
||||||
|
| || 0x0804877c lea eax, [local_10h]
|
||||||
|
| || 0x0804877f push eax
|
||||||
|
| || 0x08048780 push str.u_c ; 0x8048cbe ; "%u%c"
|
||||||
|
| || 0x08048785 call sym.imp.__isoc99_scanf ; 读入 text_size
|
||||||
|
| || 0x0804878a add esp, 0x10
|
||||||
|
| || 0x0804878d movzx eax, byte [local_1ch]
|
||||||
|
| || 0x08048791 mov eax, dword [eax*4 + 0x804b080] ; [0x804b080:4]=0
|
||||||
|
| || 0x08048798 mov eax, dword [eax] ; 取出 store[i]->desc
|
||||||
|
| || 0x0804879a mov edx, eax
|
||||||
|
| || 0x0804879c mov eax, dword [local_10h] ; 取出 test_size
|
||||||
|
| || 0x0804879f add edx, eax ; store[i]->desc + test_size
|
||||||
|
| || 0x080487a1 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x080487a5 mov eax, dword [eax*4 + 0x804b080] ; 取出 store[i]
|
||||||
|
| || 0x080487ac sub eax, 4 ; store[i] - 4
|
||||||
|
| || 0x080487af cmp edx, eax ; 比较 (store[i]->desc + test_size) 和 (store[i] - 4)
|
||||||
|
| ,===< 0x080487b1 jb 0x80487cd ; 小于时跳转
|
||||||
|
| ||| 0x080487b3 sub esp, 0xc ; 否则继续,程序退出
|
||||||
|
| ||| 0x080487b6 push str.my_l33t_defenses_cannot_be_fooled__cya ; 0x8048cc4 ; "my l33t defenses cannot be fooled, cya!"
|
||||||
|
| ||| 0x080487bb call sym.imp.puts ; int puts(const char *s)
|
||||||
|
| ||| 0x080487c0 add esp, 0x10
|
||||||
|
| ||| 0x080487c3 sub esp, 0xc
|
||||||
|
| ||| 0x080487c6 push 1 ; 1
|
||||||
|
| ||| 0x080487c8 call sym.imp.exit ; void exit(int status)
|
||||||
|
| ||| ; JMP XREF from 0x080487b1 (sub.text_length:_724)
|
||||||
|
| `---> 0x080487cd sub esp, 0xc
|
||||||
|
| || 0x080487d0 push str.text: ; 0x8048cec ; "text: "
|
||||||
|
| || 0x080487d5 call sym.imp.printf ; int printf(const char *format)
|
||||||
|
| || 0x080487da add esp, 0x10
|
||||||
|
| || 0x080487dd mov eax, dword [local_10h]
|
||||||
|
| || 0x080487e0 lea edx, [eax + 1] ; test_size + 1
|
||||||
|
| || 0x080487e3 movzx eax, byte [local_1ch]
|
||||||
|
| || 0x080487e7 mov eax, dword [eax*4 + 0x804b080] ; [0x804b080:4]=0
|
||||||
|
| || 0x080487ee mov eax, dword [eax] ; 取出 store[i]->desc
|
||||||
|
| || 0x080487f0 sub esp, 8
|
||||||
|
| || 0x080487f3 push edx
|
||||||
|
| || 0x080487f4 push eax
|
||||||
|
| || 0x080487f5 call sub.fgets_6bb ; 读入 test_size+1 个字符到 store[i]->desc
|
||||||
|
| || 0x080487fa add esp, 0x10
|
||||||
|
| ,===< 0x080487fd jmp 0x8048803
|
||||||
|
| ||| ; JMP XREF from 0x08048745 (sub.text_length:_724)
|
||||||
|
| ||`-> 0x080487ff nop
|
||||||
|
| ||,=< 0x08048800 jmp 0x8048803
|
||||||
|
| ||| ; JMP XREF from 0x08048758 (sub.text_length:_724)
|
||||||
|
| |`--> 0x08048802 nop
|
||||||
|
| | | ; JMP XREF from 0x08048800 (sub.text_length:_724)
|
||||||
|
| | | ; JMP XREF from 0x080487fd (sub.text_length:_724)
|
||||||
|
| `-`-> 0x08048803 mov eax, dword [local_ch]
|
||||||
|
| 0x08048806 xor eax, dword gs:[0x14]
|
||||||
|
| ,=< 0x0804880d je 0x8048814
|
||||||
|
| | 0x0804880f call sym.imp.__stack_chk_fail ; void __stack_chk_fail(void)
|
||||||
|
| | ; JMP XREF from 0x0804880d (sub.text_length:_724)
|
||||||
|
| `-> 0x08048814 leave
|
||||||
|
\ 0x08048815 ret
|
||||||
|
```
|
||||||
|
该函数读入新的 text_size,并使用 `(store[i]->desc + test_size) < (store[i] - 4)` 的条件来防止堆溢出,最后读入新的 description。
|
||||||
|
|
||||||
|
然而这种检查方式是有问题的,它基于 description 正好位于 user 前面这种设定。根据我们对堆分配器的理解,这个设定不一定成立,它们之间可能会包含其他已分配的堆块,从而绕过检查。
|
||||||
|
|
||||||
|
|
||||||
## Exploit
|
## Exploit
|
||||||
|
|
||||||
|
|||||||
@ -1,4 +0,0 @@
|
|||||||
# 8.1.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks
|
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
|
||||||
@ -1 +0,0 @@
|
|||||||
# 8.1.6 Hacking Blind
|
|
||||||
14
doc/8.10_aeg.md
Normal file
@ -0,0 +1,14 @@
|
|||||||
|
# 8.10 AEG: Automatic Exploit Generation
|
||||||
|
|
||||||
|
## 简介
|
||||||
|
这篇论文
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|

|
||||||
1
doc/8.11_aslp.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.11 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software
|
||||||
1
doc/8.12_aslr_on_the_line.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.12 ASLR on the Line: Practical Cache Attacks on the MMU
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.3 New Frontiers of Reverse Engineering
|
# 8.13 New Frontiers of Reverse Engineering
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -24,9 +24,9 @@ Reverse engineering is a key supporting technology to deal with systems that hav
|
|||||||
#### Previous reverse engineering
|
#### Previous reverse engineering
|
||||||
Reverse engineering has been traditionally viewed as a two step process: information extraction and abstraction.
|
Reverse engineering has been traditionally viewed as a two step process: information extraction and abstraction.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
The discussion of the main achievements of reverse engineering in last 10 years is organized three main threads:
|
The discussion of the main achievements of reverse engineering in last 10 years is organized three main threads:
|
||||||
- program analysis and its applications
|
- program analysis and its applications
|
||||||
@ -98,4 +98,4 @@ The challenges for reverse engineering:
|
|||||||
2. the need for a full integration of reverse engineering with the development process, which will benefit from on-the-fly application of reverse engineering techniques while a developer is writing the code, working on a design model, etc.
|
2. the need for a full integration of reverse engineering with the development process, which will benefit from on-the-fly application of reverse engineering techniques while a developer is writing the code, working on a design model, etc.
|
||||||
|
|
||||||
## Final
|
## Final
|
||||||

|

|
||||||
1
doc/8.14_detecting_memory_allocators.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.14 Who Allocated My Memory? Detecting Custom Memory Allocators in C Binaries
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.4 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning
|
# 8.15 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -27,7 +27,7 @@ Since our aim is to perform experiments to compare emulator based detection with
|
|||||||
- Outgoing sms messages using adb shell.
|
- Outgoing sms messages using adb shell.
|
||||||
- Populate the phone SD card with other assets.
|
- Populate the phone SD card with other assets.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Features extraction
|
#### Features extraction
|
||||||
After using DynaLog, the outputs are pre-procesed into a file of feature vectors representing the features extracted from each application. Then use InfoGain feature ranking algorithm in WEKA to get the top 100 ranked features.
|
After using DynaLog, the outputs are pre-procesed into a file of feature vectors representing the features extracted from each application. Then use InfoGain feature ranking algorithm in WEKA to get the top 100 ranked features.
|
||||||
@ -59,13 +59,13 @@ Five metrics were used for the performance emulation of the detection approaches
|
|||||||
|
|
||||||
#### Experiment 1: Emulator vs Device analysis and feature extraction
|
#### Experiment 1: Emulator vs Device analysis and feature extraction
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Experiment 2: Emulator vs Device Machine learning detection comparison
|
#### Experiment 2: Emulator vs Device Machine learning detection comparison
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
>Our experiments showed that several features were extractedmore effectively fromthe phone than the emulator using the same dataset. Furthermore, 23.8% more apps were fully analyzed on the phone compared to emulator.
|
>Our experiments showed that several features were extractedmore effectively fromthe phone than the emulator using the same dataset. Furthermore, 23.8% more apps were fully analyzed on the phone compared to emulator.
|
||||||
|
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.5 DynaLog: An automated dynamic analysis framework for characterizing Android applications
|
# 8.16 DynaLog: An automated dynamic analysis framework for characterizing Android applications
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -22,7 +22,7 @@ DynaLog has several components:
|
|||||||
4. Application trigger/exerciser
|
4. Application trigger/exerciser
|
||||||
5. Log parsing and processing scripts
|
5. Log parsing and processing scripts
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Dynamic analysis tool (DroidBox capabilities)
|
#### Dynamic analysis tool (DroidBox capabilities)
|
||||||
- An open source tool used to extract some high level behaviour and characteristics by running the app on an Android device emulator or (AVD).
|
- An open source tool used to extract some high level behaviour and characteristics by running the app on an Android device emulator or (AVD).
|
||||||
@ -46,17 +46,17 @@ DynaLog has several components:
|
|||||||
|
|
||||||
#### Experiment 1: evaluating high level behaviour features
|
#### Experiment 1: evaluating high level behaviour features
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Experiment 2: evaluating extended features and sandbox enhancements within DynaLog
|
#### Experiment 2: evaluating extended features and sandbox enhancements within DynaLog
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Results
|
#### Results
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
## What is your analysis of the identified problem, idea and evaluation?
|
## What is your analysis of the identified problem, idea and evaluation?
|
||||||
- DynaLog suffers from the same limitations of other dynamic analysis tools.
|
- DynaLog suffers from the same limitations of other dynamic analysis tools.
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.6 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls
|
# 8.17 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -16,7 +16,7 @@ Some traditional detection methods only consider the requested permissions and i
|
|||||||
## What is the proposed solution?
|
## What is the proposed solution?
|
||||||
> We present a machine learning detection method which is based on the actually used permission combinations and API calls.
|
> We present a machine learning detection method which is based on the actually used permission combinations and API calls.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
The framework contains mainly four parts:
|
The framework contains mainly four parts:
|
||||||
1. Extracting AndroidManifest.xml and Smali codes by Apktool.
|
1. Extracting AndroidManifest.xml and Smali codes by Apktool.
|
||||||
@ -34,11 +34,11 @@ The authors collected a total of 2375 Android applications. the 1170 malware sam
|
|||||||
|
|
||||||
From the feature extraction, there is some differences between requested permissions and actually used permissions, it is imporant to improve the efficiency:
|
From the feature extraction, there is some differences between requested permissions and actually used permissions, it is imporant to improve the efficiency:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
The experiments show that the feature of actually used permissions combination an API calls can achieve better performance:
|
The experiments show that the feature of actually used permissions combination an API calls can achieve better performance:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## What is your analysis of the identified problem, idea and evaluation?
|
## What is your analysis of the identified problem, idea and evaluation?
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.7 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models
|
# 8.18 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -27,7 +27,7 @@ MaMaDroid is build by combining four different phases:
|
|||||||
- Markov Chain modelling: all the samples got their sequences of abstracted calls, and these sequences can be modelled as transitions among states of a Markov Chain.
|
- Markov Chain modelling: all the samples got their sequences of abstracted calls, and these sequences can be modelled as transitions among states of a Markov Chain.
|
||||||
- Classification: Given the probabilities of transition between states of the chains as features set, we apply machine learning to detect malicious apps.
|
- Classification: Given the probabilities of transition between states of the chains as features set, we apply machine learning to detect malicious apps.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Call Graph Extraction
|
#### Call Graph Extraction
|
||||||
Static analysis apk using the [Soot](https://sable.github.io/soot/) framework to extract call graphs and [FlowDroid](https://blogs.uni-paderborn.de/sse/tools/flowdroid/) to ensure contexts and flows are preserved.
|
Static analysis apk using the [Soot](https://sable.github.io/soot/) framework to extract call graphs and [FlowDroid](https://blogs.uni-paderborn.de/sse/tools/flowdroid/) to ensure contexts and flows are preserved.
|
||||||
@ -46,9 +46,9 @@ The system operate in one of two modes by abstracting each call to either its pa
|
|||||||
#### Markov Chain Modeling
|
#### Markov Chain Modeling
|
||||||
Now it builds a Markov chain where each package/family is a state and the transitions represent the probability of moving from one state to another.
|
Now it builds a Markov chain where each package/family is a state and the transitions represent the probability of moving from one state to another.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
>Next, we use the probabilities of transi-tioning from one state (abstracted call) to another in the Markov chain as the feature vector of each app. States that are not present in a chain are represented as 0 in the feature vector. Also note that the vector derived from the Markov chain depends on the operational mode of MAMADROID. With families, there are 11 possible states, thus 121 possible transitions in each chain, while, when abstracting to packages, there are 340 states and 115,600 possible transitions.
|
>Next, we use the probabilities of transi-tioning from one state (abstracted call) to another in the Markov chain as the feature vector of each app. States that are not present in a chain are represented as 0 in the feature vector. Also note that the vector derived from the Markov chain depends on the operational mode of MAMADROID. With families, there are 11 possible states, thus 121 possible transitions in each chain, while, when abstracting to packages, there are 340 states and 115,600 possible transitions.
|
||||||
|
|
||||||
@ -63,13 +63,13 @@ The authors gathered a collection of 43,490 Android apps, 8,447 benign and 35,49
|
|||||||
|
|
||||||
The authors used the F-Measure to evaluate our system through 3 different kinds of tests: testing on samples from the same databases of the training set, testing on newer samples than the ones used for the training set, and testing on older samples than the ones used for the training set.
|
The authors used the F-Measure to evaluate our system through 3 different kinds of tests: testing on samples from the same databases of the training set, testing on newer samples than the ones used for the training set, and testing on older samples than the ones used for the training set.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
>As Android evolves over the years, so do the characteristics of both benign and malicious apps. Such evolution must be taken into account when evaluating Android malware detection systems, since their accuracy might significantly be affected as newer APIs are released and/or as malicious developers modify their strategies in order to avoid detection. Evaluating this aspect constitutes one of our research questions, and one of the reasons why our datasets span across multiple years (2010–2016).
|
>As Android evolves over the years, so do the characteristics of both benign and malicious apps. Such evolution must be taken into account when evaluating Android malware detection systems, since their accuracy might significantly be affected as newer APIs are released and/or as malicious developers modify their strategies in order to avoid detection. Evaluating this aspect constitutes one of our research questions, and one of the reasons why our datasets span across multiple years (2010–2016).
|
||||||
|
|
||||||
Testing on samples newer than the training ones (figure below, on the left) helps understanding if the system is resilient to changes in time, or if it needs constant retraining.
|
Testing on samples newer than the training ones (figure below, on the left) helps understanding if the system is resilient to changes in time, or if it needs constant retraining.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
It also set to verify whether older malware samples can still be detected, with similar F-measure scores across the years ranging from 95-97% in package mode.
|
It also set to verify whether older malware samples can still be detected, with similar F-measure scores across the years ranging from 95-97% in package mode.
|
||||||
|
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.8 DroidNative: Semantic-Based Detection of Android Native Code Malware
|
# 8.19 DroidNative: Semantic-Based Detection of Android Native Code Malware
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -24,7 +24,7 @@ the plethora of more sophisticated detectors making use of static analysis techn
|
|||||||
#### MAIL
|
#### MAIL
|
||||||
DroidNative uses MAIL (Malware Analysis Intermediate Language) to provide an abstract representation of an assembly program, and that representation is used for malware analysis and detection.
|
DroidNative uses MAIL (Malware Analysis Intermediate Language) to provide an abstract representation of an assembly program, and that representation is used for malware analysis and detection.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### Disassembler
|
#### Disassembler
|
||||||
- A challenge is ensuring that all code is found and disassembled.
|
- A challenge is ensuring that all code is found and disassembled.
|
||||||
@ -46,12 +46,12 @@ The MAIL Generator translates an assembly program to a MAIL program.
|
|||||||
#### ACFG
|
#### ACFG
|
||||||
A CFG is built for each function in the an- notated MAIL program, yielding the ACFGs.
|
A CFG is built for each function in the an- notated MAIL program, yielding the ACFGs.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
#### SWOD
|
#### SWOD
|
||||||
Each MAIL pattern is assigned a weight based on the SWOD that represents the differences between malware and benign samples’ MAIL patterns’ distributions.
|
Each MAIL pattern is assigned a weight based on the SWOD that represents the differences between malware and benign samples’ MAIL patterns’ distributions.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## What is the work's evaluation of the proposed solution?
|
## What is the work's evaluation of the proposed solution?
|
||||||
@ -61,7 +61,7 @@ Each MAIL pattern is assigned a weight based on the SWOD that represents the dif
|
|||||||
#### N-Fold Cross Validation
|
#### N-Fold Cross Validation
|
||||||
The authors use n-flod cross validation to estimate the performance and define the following evaluation metrics: DR, FPR, ROC, AUC.
|
The authors use n-flod cross validation to estimate the performance and define the following evaluation metrics: DR, FPR, ROC, AUC.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## What is your analysis of the identified problem, idea and evaluation?
|
## What is your analysis of the identified problem, idea and evaluation?
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.1.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)
|
# 8.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
## 简介
|
||||||
@ -26,7 +26,7 @@
|
|||||||
## 寻找指令序列
|
## 寻找指令序列
|
||||||
为了完成指令序列的构建,首先需要在 libc 中找到一些以 return 指令结尾,并且在执行时必然以 return 结束,而不会跳到其它地方的小工具(gadgets),算法如下:
|
为了完成指令序列的构建,首先需要在 libc 中找到一些以 return 指令结尾,并且在执行时必然以 return 结束,而不会跳到其它地方的小工具(gadgets),算法如下:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
大概就是扫描二进制找到 ret 指令,将其作为 trie 的根节点,然后回溯解析前面的指令,如果是有效指令,将其添加为子节点,再判断是否为 boring,如果不是,就继续递归回溯。举个例子,在一个 trie 中一个表示 `pop %eax` 的节点是表示 `ret` 的根节点的子节点,则这个 gadgets 为 `pop %eax; ret`。如此就能把有用的 gadgets 都找出来。
|
大概就是扫描二进制找到 ret 指令,将其作为 trie 的根节点,然后回溯解析前面的指令,如果是有效指令,将其添加为子节点,再判断是否为 boring,如果不是,就继续递归回溯。举个例子,在一个 trie 中一个表示 `pop %eax` 的节点是表示 `ret` 的根节点的子节点,则这个 gadgets 为 `pop %eax; ret`。如此就能把有用的 gadgets 都找出来。
|
||||||
|
|
||||||
@ -1 +0,0 @@
|
|||||||
# 8.2.1 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)
|
|
||||||
@ -1,3 +0,0 @@
|
|||||||
# 8.2.3 AEG: Automatic Exploit Generation
|
|
||||||
|
|
||||||
## 简介
|
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.9 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware
|
# 8.20 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware
|
||||||
|
|
||||||
|
|
||||||
## What is your take-away message from this paper?
|
## What is your take-away message from this paper?
|
||||||
@ -14,7 +14,7 @@ An effective analytic system needs to address the following questions:
|
|||||||
|
|
||||||
## What is the proposed solution?
|
## What is the proposed solution?
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
The system consists these modules:
|
The system consists these modules:
|
||||||
- Extensible Crawler: systematically build up the mobile applications database for malware analysis and association.
|
- Extensible Crawler: systematically build up the mobile applications database for malware analysis and association.
|
||||||
@ -29,9 +29,9 @@ The system consists these modules:
|
|||||||
- Generate Lev2 signature: generate the Lev2 signature for each class based on the Lev3 signature of methods within that class.
|
- Generate Lev2 signature: generate the Lev2 signature for each class based on the Lev3 signature of methods within that class.
|
||||||
- Generate Lev1 signature: based on the Lev2 signatures.
|
- Generate Lev1 signature: based on the Lev2 signatures.
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
## What is the work's evaluation of the proposed solution?
|
## What is the work's evaluation of the proposed solution?
|
||||||
1
doc/8.21_tracing_to_detect_spraying.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.21 Micro-Virtualization Memory Tracing to Detect and Prevent Spraying Attacks
|
||||||
1
doc/8.22_memory_checking.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.22 Practical Memory Checking With Dr. Memory
|
||||||
1
doc/8.23_current_anti-rop.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.23 Evaluating the Effectiveness of Current Anti-ROP Defenses
|
||||||
1
doc/8.24_runtime_re-randomization.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.24 How to Make ASLR Win the Clone Wars: Runtime Re-Randomization
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.1.2 Return-Oriented Programming without Returns
|
# 8.2 Return-Oriented Programming without Returns
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
## 简介
|
||||||
@ -41,7 +41,7 @@ blx r5
|
|||||||
|
|
||||||
跳转攻击流程的原理如下图所示:
|
跳转攻击流程的原理如下图所示:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
在 x86 上,我们使用一个寄存器 y 保存 trampoline 的地址,那么以间接跳转到 y 结束的指令序列的行为就像是以一个 update-load-branch 指令结束一样。并形成像 ROP 链一样的东西。这种操作在 ARM 上也是类似的。
|
在 x86 上,我们使用一个寄存器 y 保存 trampoline 的地址,那么以间接跳转到 y 结束的指令序列的行为就像是以一个 update-load-branch 指令结束一样。并形成像 ROP 链一样的东西。这种操作在 ARM 上也是类似的。
|
||||||
|
|
||||||
@ -67,4 +67,4 @@ pop %eax; jmp *(%eax)
|
|||||||
|
|
||||||
下图是一个函数调用的示例:
|
下图是一个函数调用的示例:
|
||||||
|
|
||||||

|

|
||||||
@ -1 +0,0 @@
|
|||||||
# 8.3.1 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software
|
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.1.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms
|
# 8.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
## 简介
|
||||||
@ -18,12 +18,12 @@
|
|||||||
|
|
||||||
内核 ROP 如下图所示:
|
内核 ROP 如下图所示:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
|
|
||||||
自动化攻击系统的结构如下图所示:
|
自动化攻击系统的结构如下图所示:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
其中的三个核心组成部分:
|
其中的三个核心组成部分:
|
||||||
- Constructor:扫描给定的二进制文件,标记出有用的指令序列,并自动构建出 gadgets
|
- Constructor:扫描给定的二进制文件,标记出有用的指令序列,并自动构建出 gadgets
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.1.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks
|
# 8.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
## 简介
|
||||||
@ -40,7 +40,7 @@ ROPdefender 同样也使用 shadow stack 来储存每次函数调用的返回地
|
|||||||
|
|
||||||
整体思想如下图所示:
|
整体思想如下图所示:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
在处理器执行指令时,对指令类别进行判断,如果是 call,将返回地址放进 shadow stack;如果是 return,则检查与 shadow stack 顶部的返回地址是否相同。这一方法不仅可用于检测 ROP 攻击,还可以检测所有利用缓冲区溢出改写返回地址的攻击。
|
在处理器执行指令时,对指令类别进行判断,如果是 call,将返回地址放进 shadow stack;如果是 return,则检查与 shadow stack 顶部的返回地址是否相同。这一方法不仅可用于检测 ROP 攻击,还可以检测所有利用缓冲区溢出改写返回地址的攻击。
|
||||||
|
|
||||||
@ -48,7 +48,7 @@ ROPdefender 同样也使用 shadow stack 来储存每次函数调用的返回地
|
|||||||
## 实现细节
|
## 实现细节
|
||||||
基于 Pin 动态二进制插桩(DBI)框架的实现如下图所示:
|
基于 Pin 动态二进制插桩(DBI)框架的实现如下图所示:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
一般工作流程是这样的,程序在 DBI 框架下加载并启动。DBI 框架确保:
|
一般工作流程是这样的,程序在 DBI 框架下加载并启动。DBI 框架确保:
|
||||||
1. 程序的每条指令都在 DBI 的控制下执行
|
1. 程序的每条指令都在 DBI 的控制下执行
|
||||||
4
doc/8.5_dop.md
Normal file
@ -0,0 +1,4 @@
|
|||||||
|
# 8.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks
|
||||||
|
|
||||||
|
|
||||||
|
## 简介
|
||||||
1
doc/8.6_brop.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.6 Hacking Blind
|
||||||
1
doc/8.7_jit-rop_defenses.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.7 What Cannot Be Read, Cannot Be Leveraged? Revisiting Assumptions of JIT-ROP Defenses
|
||||||
1
doc/8.8_dynamic_taint_analysis.md
Normal file
@ -0,0 +1 @@
|
|||||||
|
# 8.8 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)
|
||||||
@ -1,4 +1,4 @@
|
|||||||
# 8.2.2 Symbolic Execution for Software Testing: Three Decades Later
|
# 8.9 Symbolic Execution for Software Testing: Three Decades Later
|
||||||
|
|
||||||
|
|
||||||
## 简介
|
## 简介
|
||||||
@ -10,7 +10,7 @@
|
|||||||
## 传统符号执行
|
## 传统符号执行
|
||||||
符号执行的关键是使用符号值替代具体的值作为输入,并将程序变量的值表示为符号输入值的符号表达式。其结果是程序计算的输出值被表示为符号输入值的函数。一个符号执行的路径就是一个 true 和 false 组成的序列,其中第 i 个 true(或false)表示在该路径的执行中遇到的第 i 个条件语句,并且走的是 then(或else) 这个分支。一个程序所有的执行路径可以用执行树(Execution Tree)来表示。举一个例子:
|
符号执行的关键是使用符号值替代具体的值作为输入,并将程序变量的值表示为符号输入值的符号表达式。其结果是程序计算的输出值被表示为符号输入值的函数。一个符号执行的路径就是一个 true 和 false 组成的序列,其中第 i 个 true(或false)表示在该路径的执行中遇到的第 i 个条件语句,并且走的是 then(或else) 这个分支。一个程序所有的执行路径可以用执行树(Execution Tree)来表示。举一个例子:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
函数 testme() 有 3 条执行路径,组成右边的执行树。只需要针对路径给出输入,即可遍历这 3 条路径,例如:{x = 0, y = 1}、{x = 2, y = 1} 和 {x = 30, y = 15}。符号执行的目标就是去生成这样的输入集合,在给定的时间内遍历所有的路径。
|
函数 testme() 有 3 条执行路径,组成右边的执行树。只需要针对路径给出输入,即可遍历这 3 条路径,例如:{x = 0, y = 1}、{x = 2, y = 1} 和 {x = 30, y = 15}。符号执行的目标就是去生成这样的输入集合,在给定的时间内遍历所有的路径。
|
||||||
|
|
||||||
@ -24,17 +24,17 @@
|
|||||||
|
|
||||||
如果符号执行的代码包含循环或递归,且它们的终止条件是符号化的,那么可能就会导致产生无数条路径。举个例子:
|
如果符号执行的代码包含循环或递归,且它们的终止条件是符号化的,那么可能就会导致产生无数条路径。举个例子:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
这段程序的执行路径有两种:一种是无数的 true 加上一个 false,另一种是无数的 false。第一种的符号路径约束如下:
|
这段程序的执行路径有两种:一种是无数的 true 加上一个 false,另一种是无数的 false。第一种的符号路径约束如下:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
其中每个 N<sub>i</sub> 都是一个新的符号值,执行结束的符号状态为 {N->N<sub>n+1</sub>, sum->Σ<sub>i∈[1,n]</sub>N<sub>i</sub>}。在实践中我们需要通过一些方法限制这样的搜索。
|
其中每个 N<sub>i</sub> 都是一个新的符号值,执行结束的符号状态为 {N->N<sub>n+1</sub>, sum->Σ<sub>i∈[1,n]</sub>N<sub>i</sub>}。在实践中我们需要通过一些方法限制这样的搜索。
|
||||||
|
|
||||||
传统符号执行的一个关键的缺点是,当符号路径约束包含了不能由约束求解器求解的公式时,就不能生成输入值。例如把上面的 twice 函数替换成下面的:
|
传统符号执行的一个关键的缺点是,当符号路径约束包含了不能由约束求解器求解的公式时,就不能生成输入值。例如把上面的 twice 函数替换成下面的:
|
||||||
|
|
||||||

|

|
||||||
|
|
||||||
那么符号执行会得到路径约束 x<sub>0</sub> ≠ (y<sub>0</sub>y<sub>0</sub>)mod50 和 x<sub>0</sub> = (y<sub>0</sub>y<sub>0</sub>)mod50。更严格一点,如果我们不知道 twice 的源码,符号执行将得到路径约束 x<sub>0</sub> ≠ twice(y<sub>0</sub>) 和 x<sub>0</sub> = twice(y<sub>0</sub>)。在这两种情况下,符号执行都不能生成输入值。
|
那么符号执行会得到路径约束 x<sub>0</sub> ≠ (y<sub>0</sub>y<sub>0</sub>)mod50 和 x<sub>0</sub> = (y<sub>0</sub>y<sub>0</sub>)mod50。更严格一点,如果我们不知道 twice 的源码,符号执行将得到路径约束 x<sub>0</sub> ≠ twice(y<sub>0</sub>) 和 x<sub>0</sub> = twice(y<sub>0</sub>)。在这两种情况下,符号执行都不能生成输入值。
|
||||||
|
|
||||||
@ -3,26 +3,27 @@
|
|||||||
论文下载:
|
论文下载:
|
||||||
链接:https://pan.baidu.com/s/1G-WFCzAU2VdrrsHqJzjGpw 密码:vhfw
|
链接:https://pan.baidu.com/s/1G-WFCzAU2VdrrsHqJzjGpw 密码:vhfw
|
||||||
|
|
||||||
* Return-Oriented Programming
|
- [8.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)](8.1_ret2libc_without_func_calls.md)
|
||||||
* [8.1.1 The Geometry of Innocent Flesh on the Bone: Return-into-libc without Function Calls (on the x86)](8.1.1_return-into-libc_without_function_calls.md)
|
- [8.2 Return-Oriented Programming without Returns](8.2_rop_without_returns.md)
|
||||||
* [8.1.2 Return-Oriented Programming without Returns](8.1.2_rop_without_returns.md)
|
- [8.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms](8.3_rop_rootkits.md)
|
||||||
* [8.1.3 Return-Oriented Rootkits: Bypassing Kernel Code Integrity Protection Mechanisms](8.1.3_return-oriented_rootkits.md)
|
- [8.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks](8.4_ropdefender.md)
|
||||||
* [8.1.4 ROPdefender: A Detection Tool to Defend Against Return-Oriented Programming Attacks](8.1.4_ropdefender.md)
|
- [8.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks](8.5_dop.md)
|
||||||
* [8.1.5 Data-Oriented Programming: On the Expressiveness of Non-Control Data Attacks](8.1.5_data-oriented_programming.md)
|
- [8.6 Hacking Blind](8.6_brop.md)
|
||||||
* [8.1.6 Hacking Blind](8.1.6_hacking_blind.md)
|
- [8.7 What Cannot Be Read, Cannot Be Leveraged? Revisiting Assumptions of JIT-ROP Defenses](8.7_jit-rop_defenses.md)
|
||||||
* Symbolic Execution
|
- [8.8 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)](8.8_dynamic_taint_analysis.md)
|
||||||
* [8.2.1 All You Ever Wanted to Know About Dynamic Taint Analysis and Forward Symbolic Execution (but might have been afraid to ask)](8.2.1_dynamic_taint_analysis.md)
|
- [8.9 Symbolic Execution for Software Testing: Three Decades Later](8.9_symbolic_execution.md)
|
||||||
* [8.2.2 Symbolic Execution for Software Testing: Three Decades Later](8.2.2_symbolic_execution_for_software_testing.md)
|
- [8.10 AEG: Automatic Exploit Generation](8.10_aeg.md)
|
||||||
* [8.2.3 AEG: Automatic Exploit Generation](8.2.3_automatic_exploit_generation.md)
|
- [8.11 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software](8.11_aslp.md)
|
||||||
* Address Space Layout Randomization
|
- [8.12 ASLR on the Line: Practical Cache Attacks on the MMU](8.12_aslr_on_the_line.md)
|
||||||
* [8.3.1 Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software](8.3.1_aslp.md)
|
- [8.13 New Frontiers of Reverse Engineering](8.13_reverse_engineering.md)
|
||||||
* Code Obfuscation
|
- [8.14 Who Allocated My Memory? Detecting Custom Memory Allocators in C Binaries](8.14_detecting_memory_allocators.md)
|
||||||
* Reverse Engineering
|
- [8.15 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning](8.15_emulator_vs_real_phone.md)
|
||||||
* [8.3 New Frontiers of Reverse Engineering](8.3_new_frontiers_of_reverse_engineering.md)
|
- [8.16 DynaLog: An automated dynamic analysis framework for characterizing Android applications](8.16_dynalog.md)
|
||||||
* Android Security
|
- [8.17 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls](8.17_actual_used_permissions.md)
|
||||||
* [8.4 EMULATOR vs REAL PHONE: Android Malware Detection Using Machine Learning](8.4_emulator_vs_real_phone.md)
|
- [8.18 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models](8.18_malware_markov_chains.md)
|
||||||
* [8.5 DynaLog: An automated dynamic analysis framework for characterizing Android applications](8.5_dynalog_an_automated_dynamic_analysis_framework.md)
|
- [8.19 DroidNative: Semantic-Based Detection of Android Native Code Malware](8.19_droidnative.md)
|
||||||
* [8.6 A Static Android Malware Detection Based on Actual Used Permissions Combination and API Calls](8.6_malware_detection_based_on_actual_used_permissions.md)
|
- [8.20 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware](8.20_droidanalytics.md)
|
||||||
* [8.7 MaMaDroid: Detecting Android malware by building Markov chains of behavioral models](8.7_detecting_malware_by_building_markov_chains.md)
|
- [8.21 Micro-Virtualization Memory Tracing to Detect and Prevent Spraying Attacks](8.21_tracing_to_detect_spraying.md)
|
||||||
* [8.8 DroidNative: Semantic-Based Detection of Android Native Code Malware](8.8_droidnative_semantic-based_detection_of_android_native_code_malware.md)
|
- [8.22 Practical Memory Checking With Dr. Memory](8.22_memory_checking.md)
|
||||||
* [8.9 DroidAnalytics: A Signature Based Analytic System to Collect, Extract, Analyze and Associate Android Malware](8.9_droidanalytics_signature_based_analytic_system.md)
|
- [8.23 Evaluating the Effectiveness of Current Anti-ROP Defenses](8.23_current_anti-rop.md)
|
||||||
|
- [8.24 How to Make ASLR Win the Clone Wars: Runtime Re-Randomization](8.24_runtime_re-randomization.md)
|
||||||
|
|||||||
|
Before 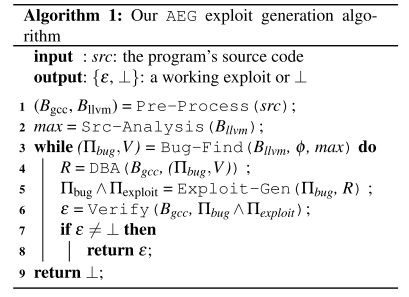
(image error) Size: 43 KiB After 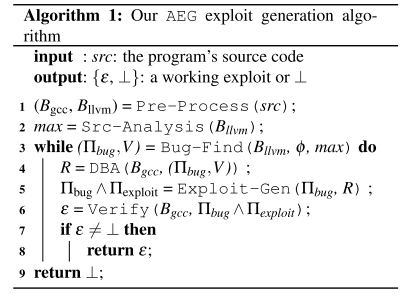
(image error) Size: 43 KiB 

|
|
Before 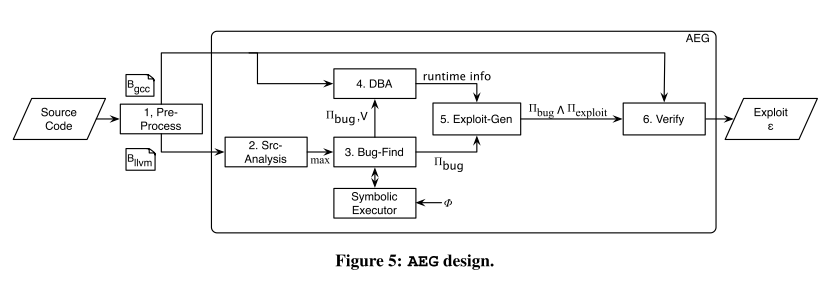
(image error) Size: 29 KiB After 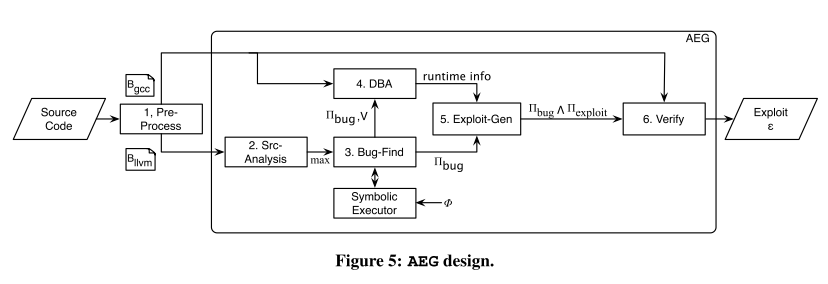
(image error) Size: 29 KiB 

|
|
Before 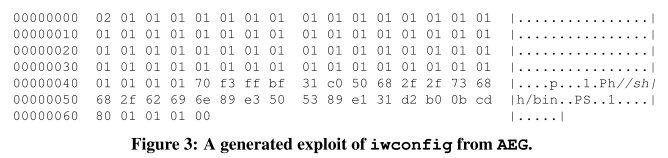
(image error) Size: 37 KiB After 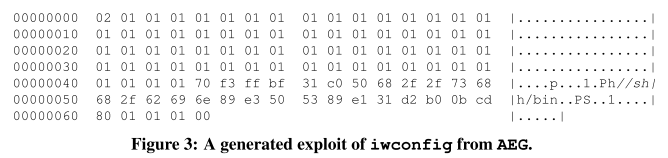
(image error) Size: 37 KiB 

|
|
Before 
(image error) Size: 56 KiB After 
(image error) Size: 56 KiB 

|
|
Before 
(image error) Size: 13 KiB After 
(image error) Size: 13 KiB 

|
|
Before 
(image error) Size: 45 KiB After 
(image error) Size: 45 KiB 

|
|
Before 
(image error) Size: 56 KiB After 
(image error) Size: 56 KiB 

|
|
Before 
(image error) Size: 24 KiB After 
(image error) Size: 24 KiB 

|
|
Before 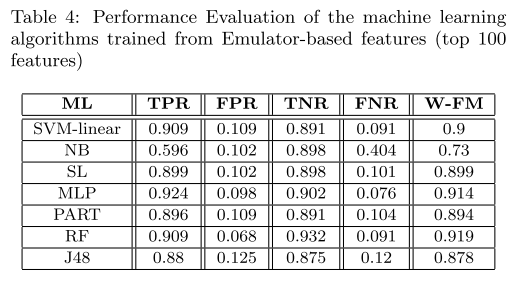
(image error) Size: 61 KiB After 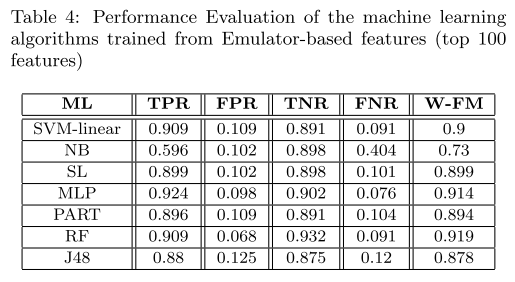
(image error) Size: 61 KiB 

|
|
Before 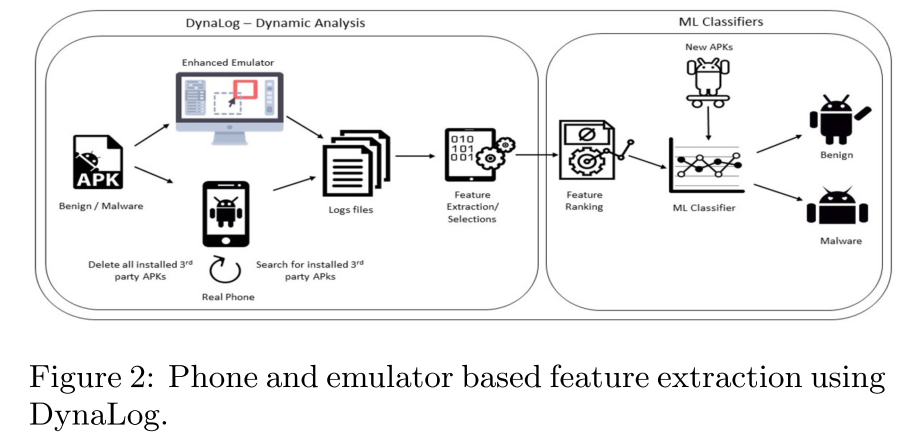
(image error) Size: 130 KiB After 
(image error) Size: 130 KiB 

|
|
Before 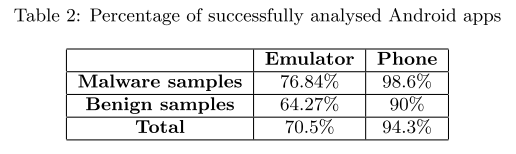
(image error) Size: 29 KiB After 
(image error) Size: 29 KiB 

|
|
Before 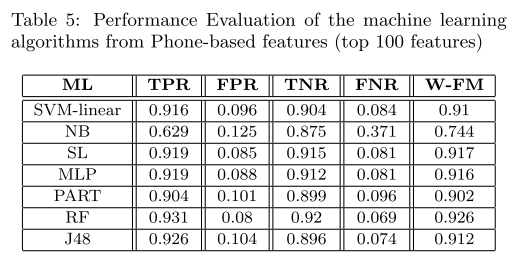
(image error) Size: 60 KiB After 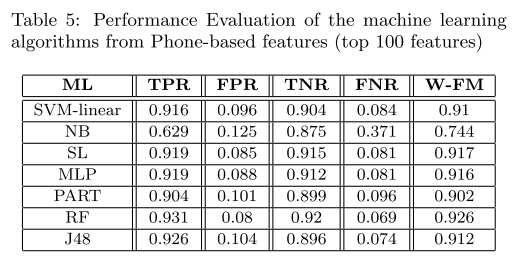
(image error) Size: 60 KiB 

|
|
Before 
(image error) Size: 111 KiB After 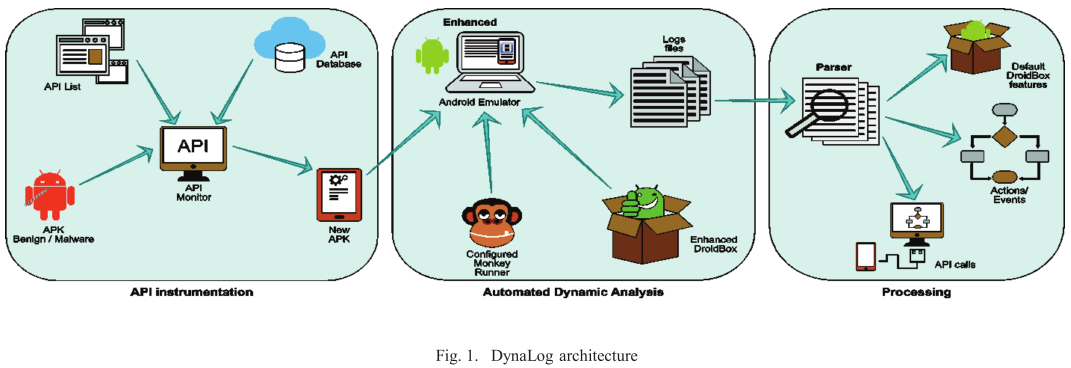
(image error) Size: 111 KiB 

|
|
Before 
(image error) Size: 84 KiB After 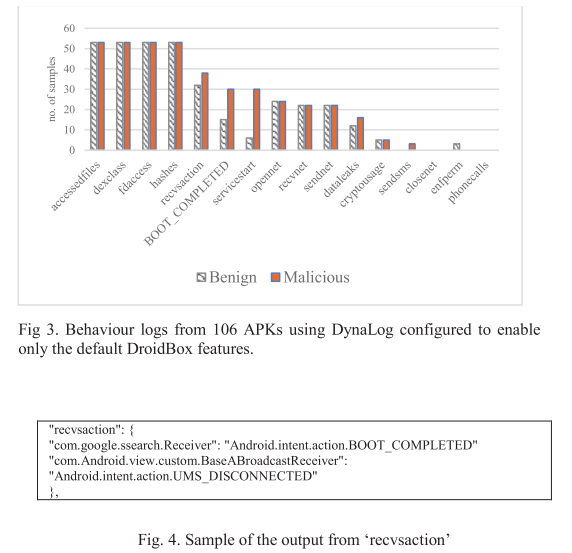
(image error) Size: 84 KiB 

|
|
Before 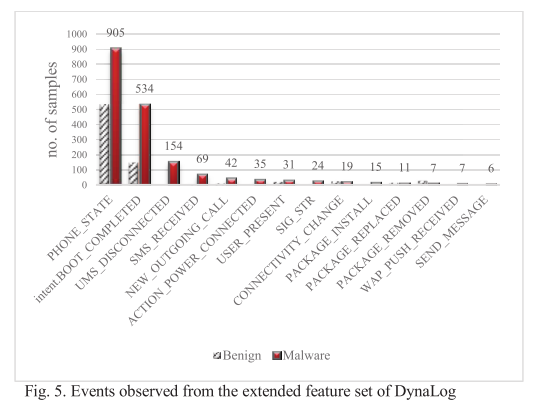
(image error) Size: 77 KiB After 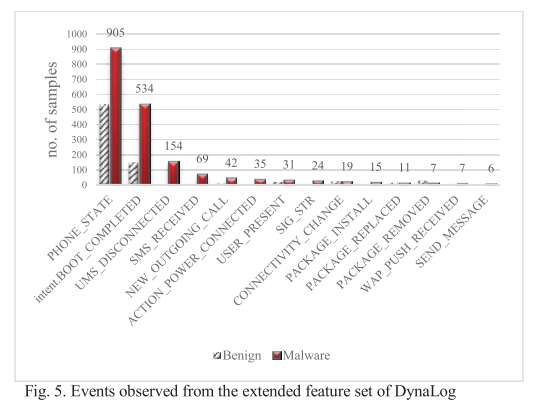
(image error) Size: 77 KiB 

|
|
Before 
(image error) Size: 51 KiB After 
(image error) Size: 51 KiB 

|
|
Before 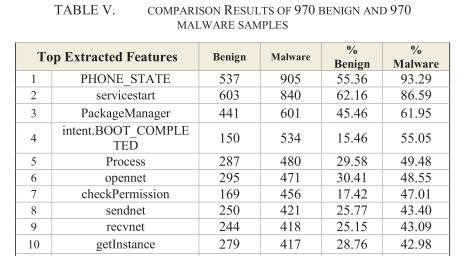
(image error) Size: 58 KiB After 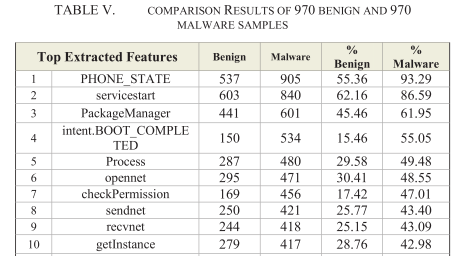
(image error) Size: 58 KiB 

|
|
Before 
(image error) Size: 187 KiB After 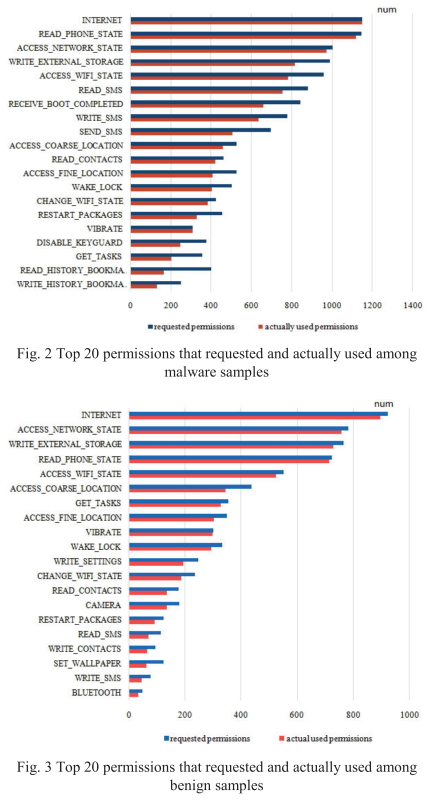
(image error) Size: 187 KiB 

|
|
Before 
(image error) Size: 176 KiB After 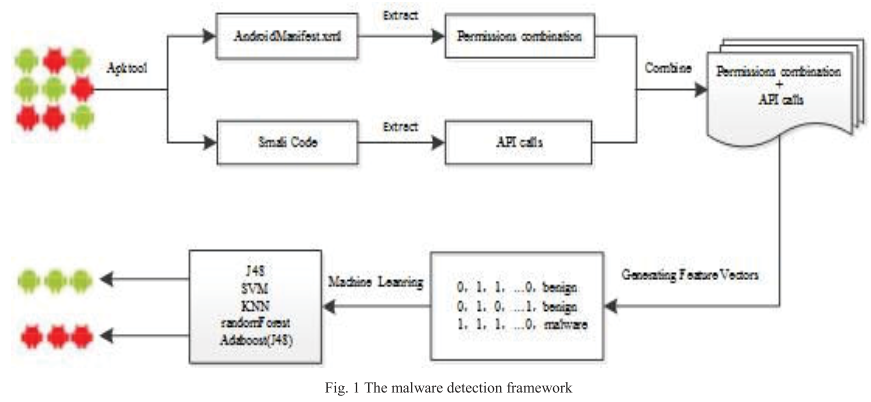
(image error) Size: 176 KiB 

|
|
Before 
(image error) Size: 53 KiB After 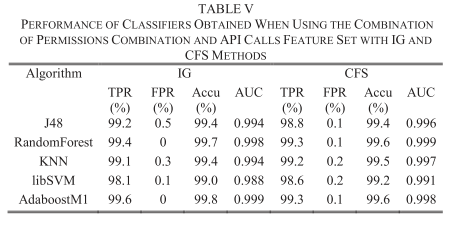
(image error) Size: 53 KiB 

|
|
Before 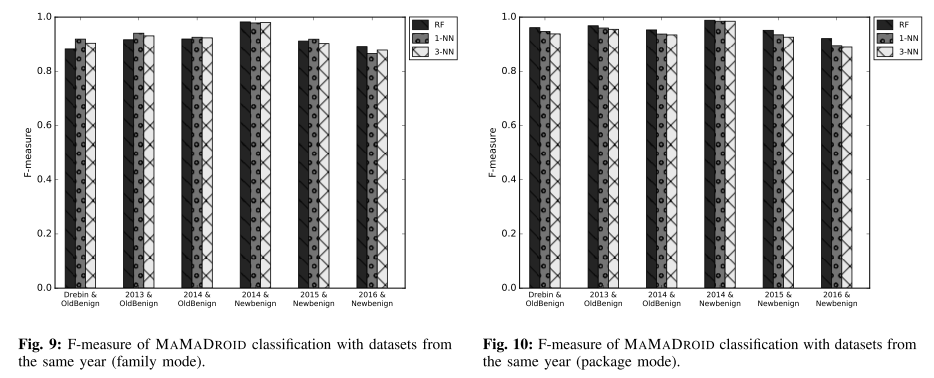
(image error) Size: 118 KiB After 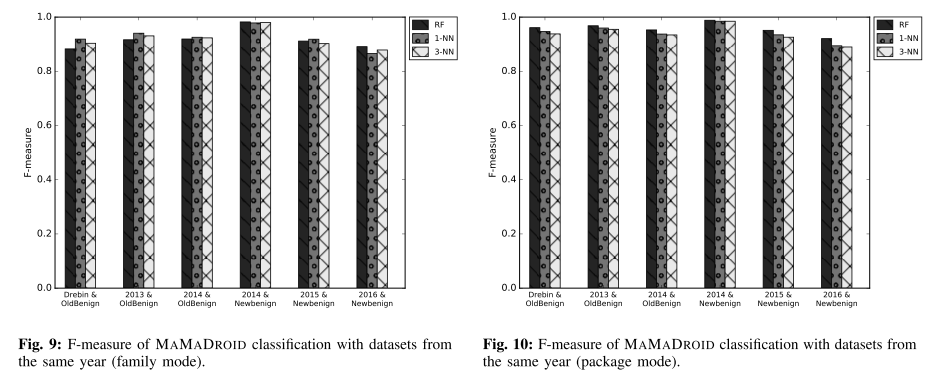
(image error) Size: 118 KiB 

|
|
Before 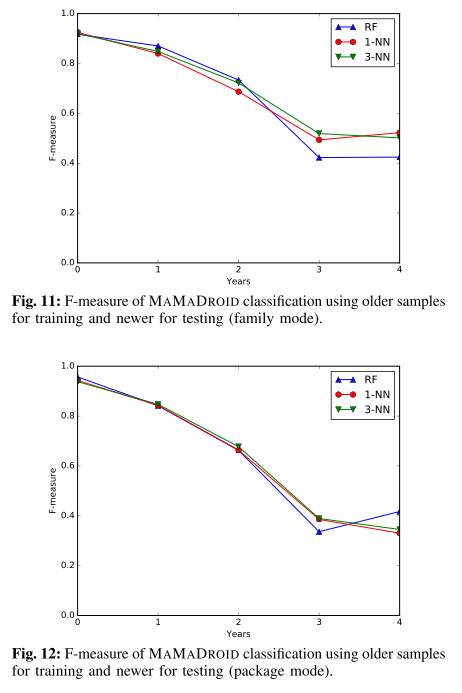
(image error) Size: 60 KiB After 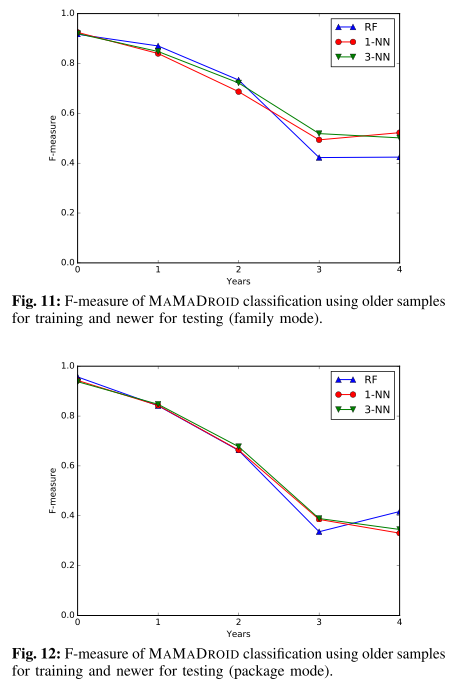
(image error) Size: 60 KiB 

|
|
Before 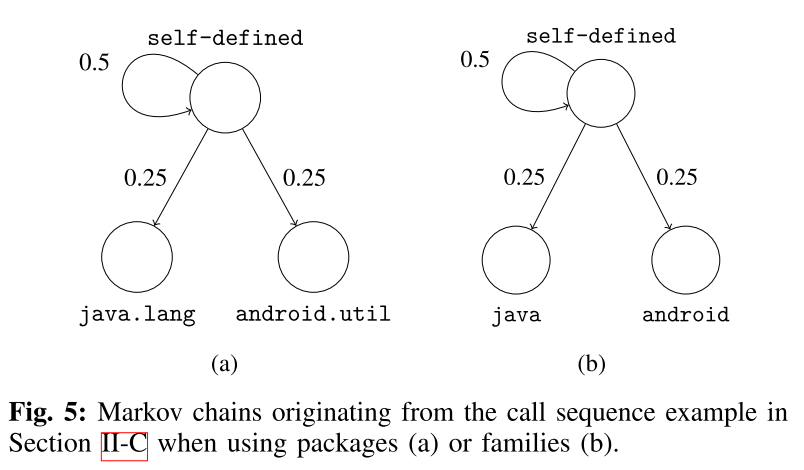
(image error) Size: 73 KiB After 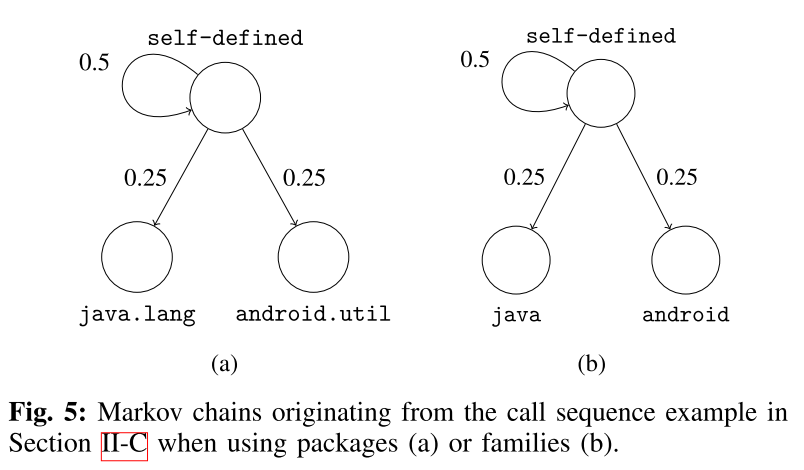
(image error) Size: 73 KiB 

|
|
Before 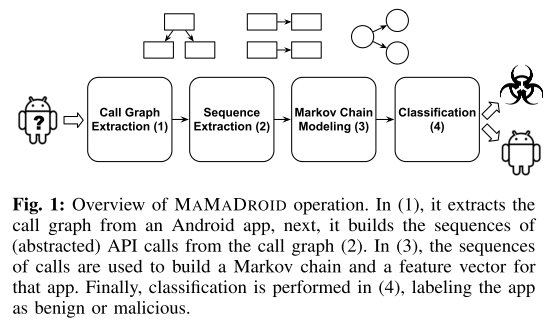
(image error) Size: 75 KiB After 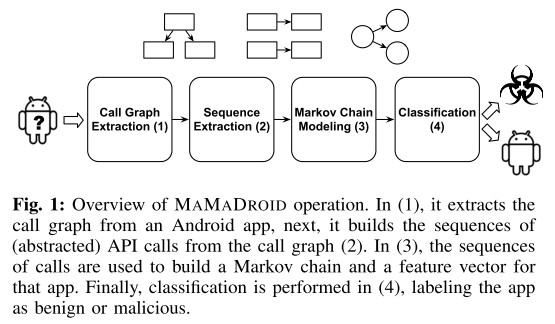
(image error) Size: 75 KiB 

|
|
Before 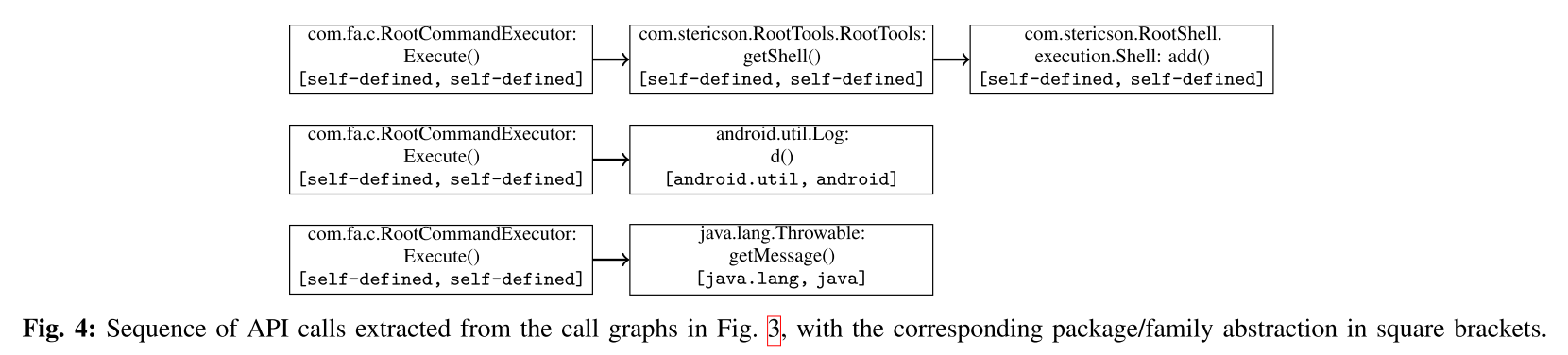
(image error) Size: 121 KiB After 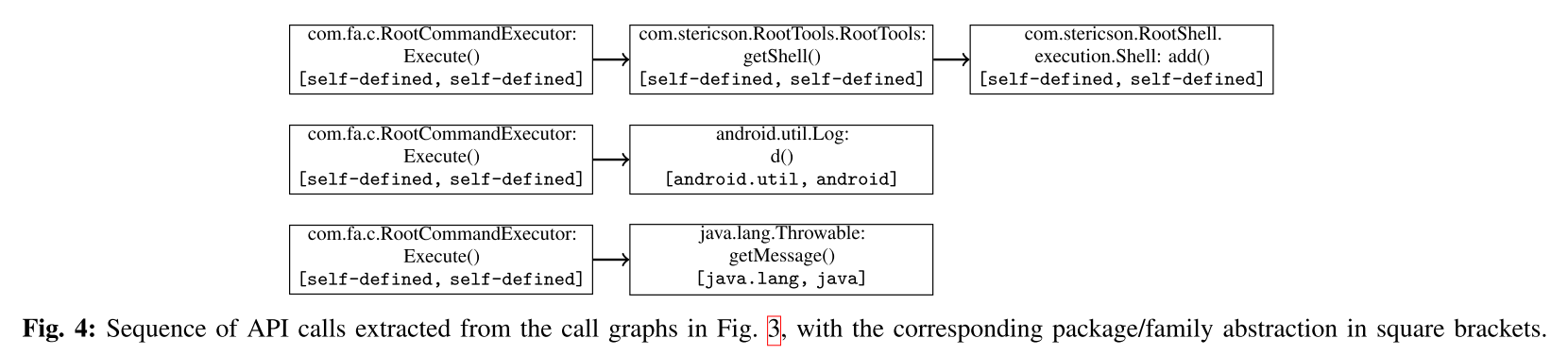
(image error) Size: 121 KiB 

|
|
Before 
(image error) Size: 67 KiB After 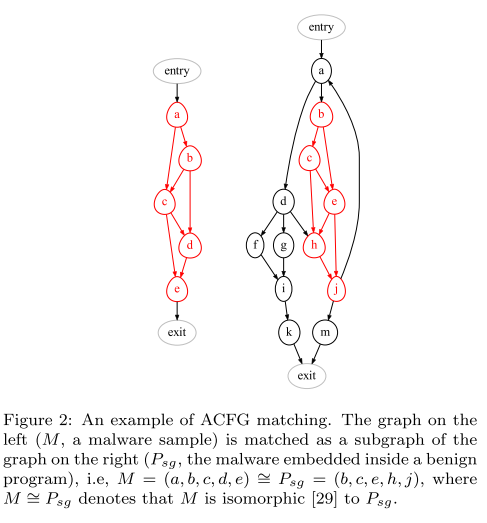
(image error) Size: 67 KiB 

|
|
Before 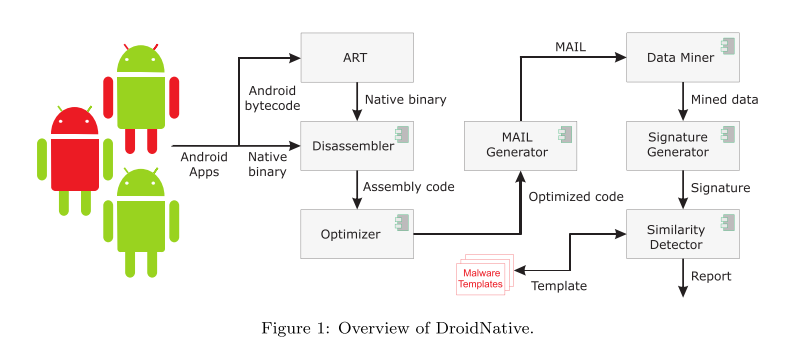
(image error) Size: 49 KiB After 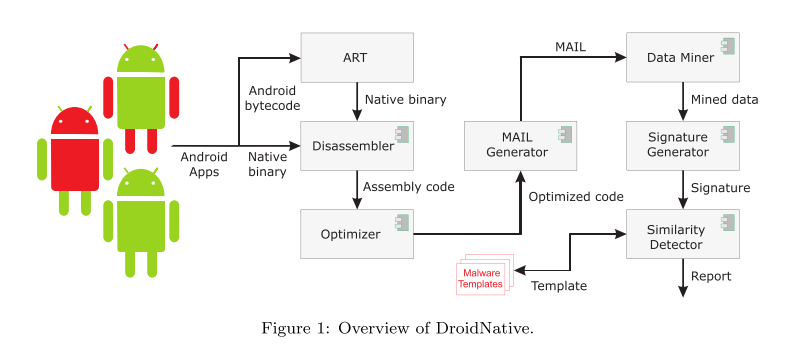
(image error) Size: 49 KiB 

|
|
Before 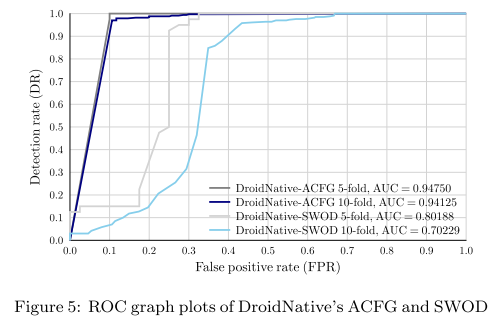
(image error) Size: 49 KiB After 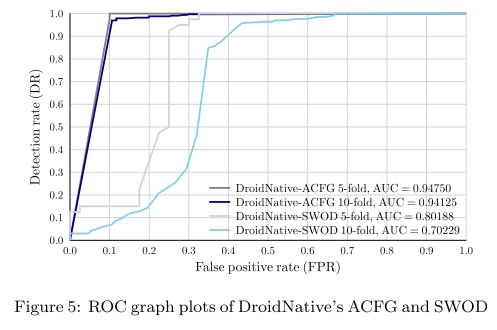
(image error) Size: 49 KiB 

|
|
Before 
(image error) Size: 75 KiB After 
(image error) Size: 75 KiB 

|
|
Before 
(image error) Size: 89 KiB After 
(image error) Size: 89 KiB 

|
|
Before 
(image error) Size: 72 KiB After 
(image error) Size: 72 KiB 

|
|
Before 
(image error) Size: 124 KiB After 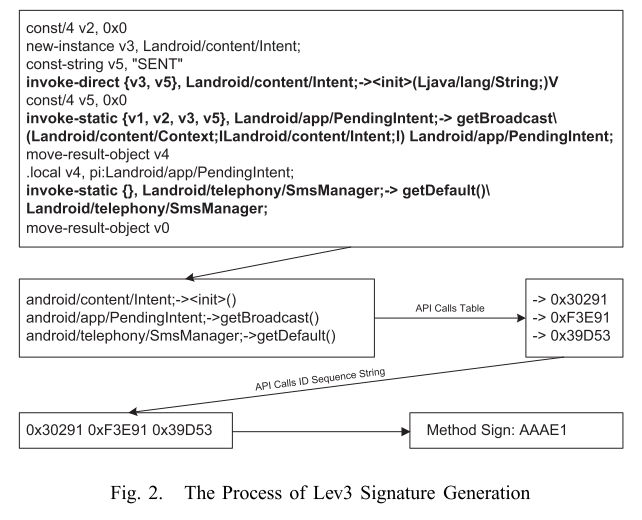
(image error) Size: 124 KiB 

|
|
Before 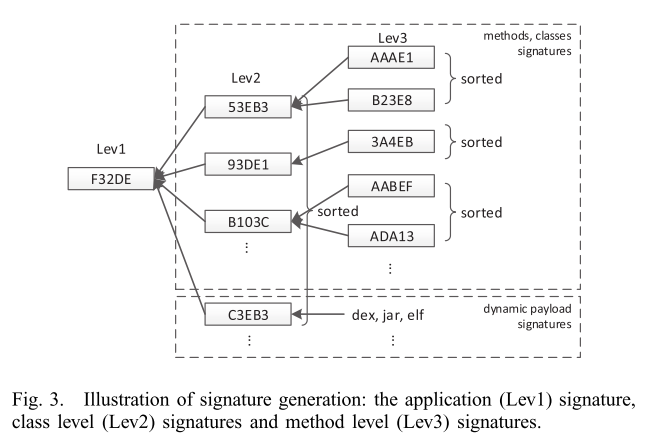
(image error) Size: 68 KiB After 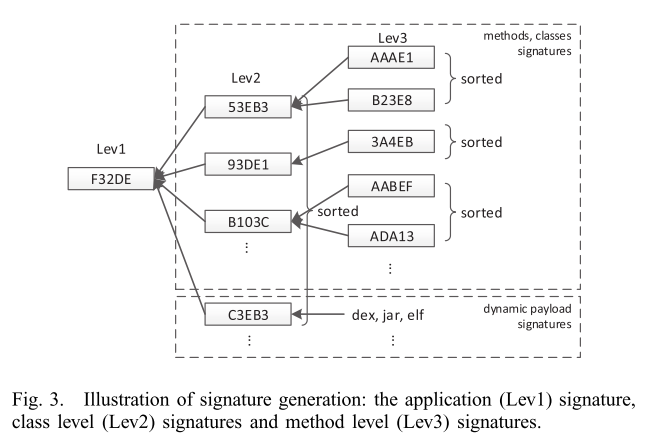
(image error) Size: 68 KiB 

|
|
Before 
(image error) Size: 181 KiB After 
(image error) Size: 181 KiB 

|
|
Before 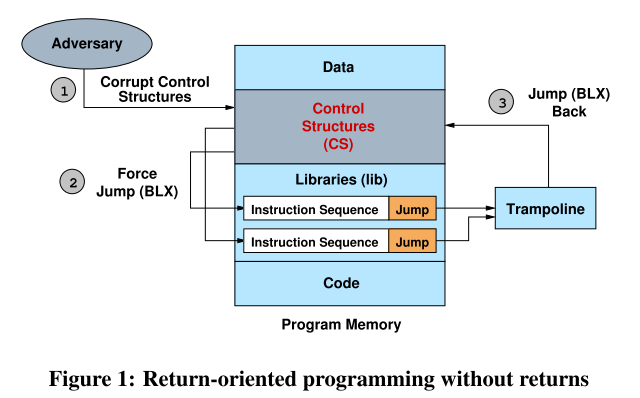
(image error) Size: 46 KiB After 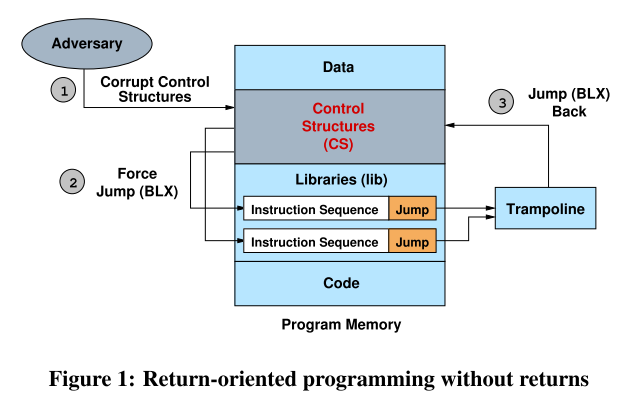
(image error) Size: 46 KiB 

|
|
Before 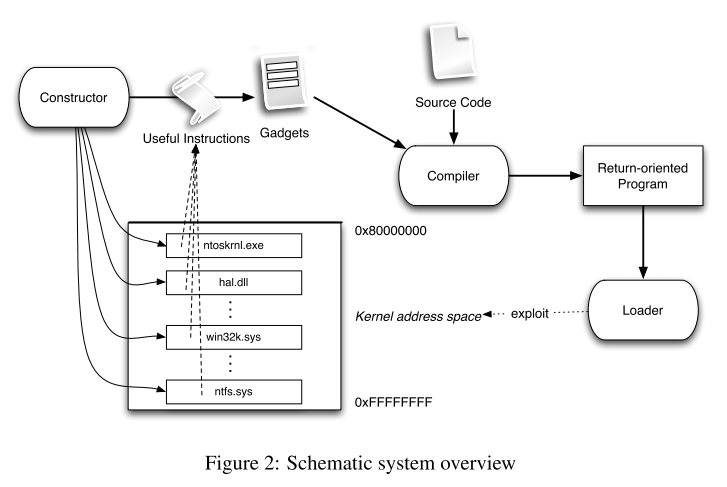
(image error) Size: 64 KiB After 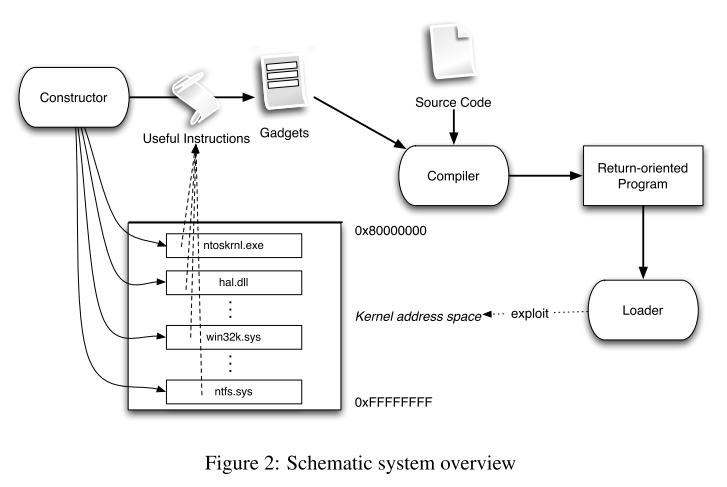
(image error) Size: 64 KiB 

|
|
Before 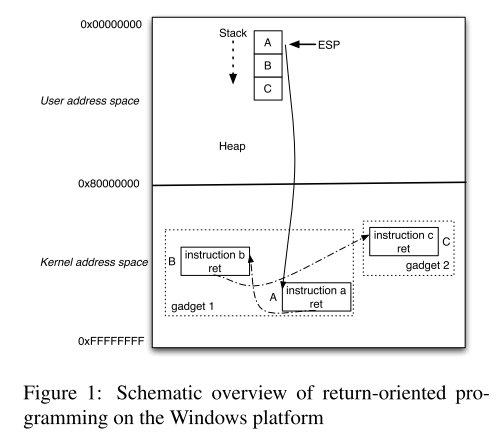
(image error) Size: 42 KiB After 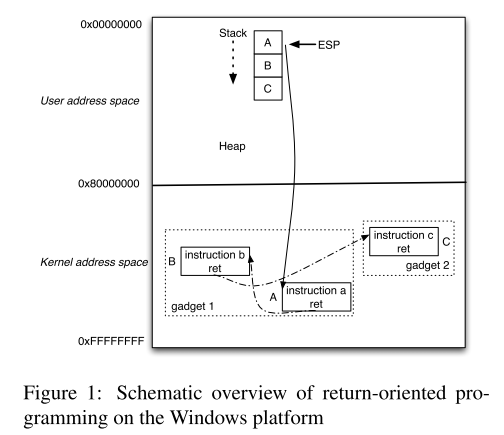
(image error) Size: 42 KiB 

|
|
Before 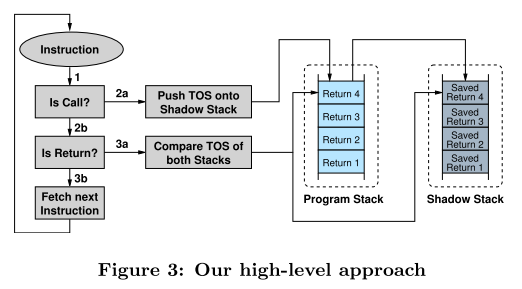
(image error) Size: 39 KiB After 
(image error) Size: 39 KiB 

|
|
Before 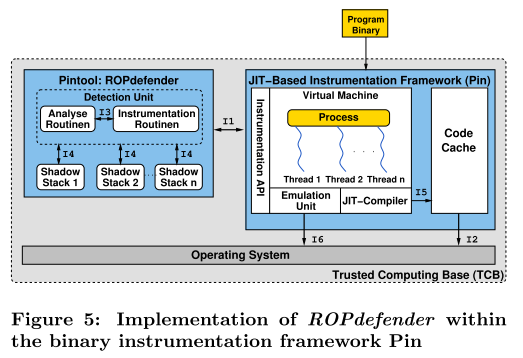
(image error) Size: 62 KiB After 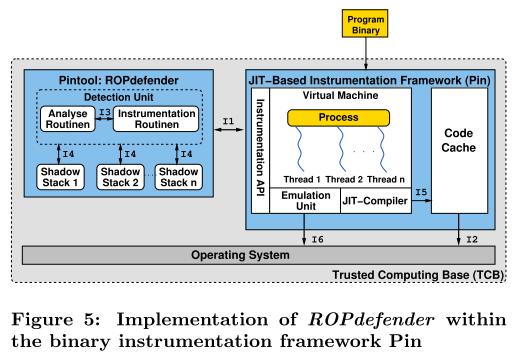
(image error) Size: 62 KiB 

|
|
Before 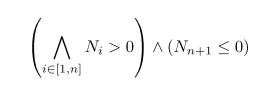
(image error) Size: 5.0 KiB After 
(image error) Size: 5.0 KiB 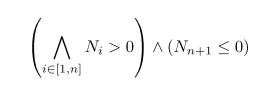

|
|
Before 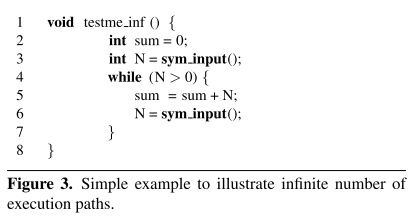
(image error) Size: 20 KiB After 
(image error) Size: 20 KiB 

|
|
Before 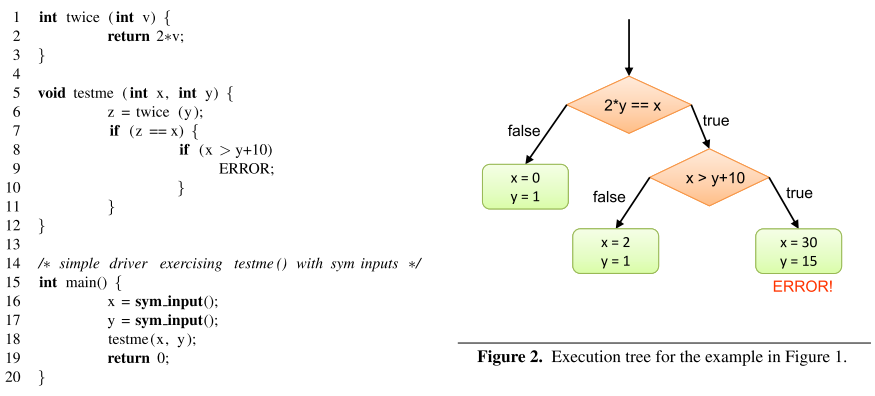
(image error) Size: 60 KiB After 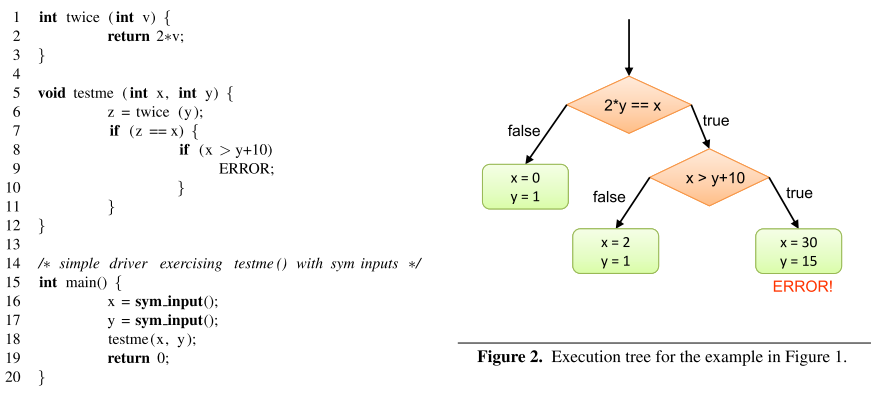
(image error) Size: 60 KiB 

|
|
Before 
(image error) Size: 18 KiB After 
(image error) Size: 18 KiB 

|